MKULTRA: The Hidden Hand | Part 3 - The Network
Technological Evolution and the Battle for Consciousness
You reach for it before your eyes are fully open. Again. Not because you want to, but because you have to. The phantom vibration in your pocket. The anxiety when your battery hits 10%. The relief of the dopamine hit when notifications appear. 144 times a day, on average. Your fingers dance across glass that knows you better than your closest friends. Touch. Scroll. Like. Refresh. Each motion a tiny surrender you never consciously agreed to.
Check email. Scan headlines. Review notifications. Open Instagram. Swipe through dating profiles. Read texts. Track steps. Monitor sleep patterns. Order food. Hail rides. Navigate cities. Post stories. Doom scroll. Reply to work messages at midnight. Capture memories. Share locations. Buy products suggested by algorithms. Stream content. Pay bills. Take selfies. Edit reality. Seek validation. Fill every moment of silence, every second of waiting, every pause in conversation.
You're not alone. 6.8 billion people perform this same digital ritual, thumbs tapping screens in synchronicity across time zones. A college student in Denver refreshes TikTok while a banker in Singapore checks market updates and a mother in Mumbai scrolls through family photos—all held captive by the same mechanism of engagement, optimized to the millisecond.
In 2007, a man in a black turtleneck and jeans introduced what he called "a revolutionary mobile phone." But Steve Jobs wasn't selling a phone any more than Ford was selling horses. He was deploying a civilian-grade neural interface—each feature carefully designed to capture and retain the most precious commodity: your attention.
While The Laboratory created the tools through systematic trauma experiments and The Theater staged the performances using celebrities as programmable conduits, The Network delivers them directly to your pocket. It represents the technological scaling of mind control - transforming what was once confined to classified facilities and entertainment industries into an ambient system that surrounds billions simultaneously. Where The Laboratory required physical access to subjects and The Theater needed cultural attention, The Network operates through devices we voluntarily carry, platforms we eagerly browse, and electromagnetic fields we can't even perceive. Every notification that interrupts your dinner conversation, every algorithm that predicts your desires before you feel them, every blue-lit hour stolen from sleep—you're not just using technology. You're immersed in a system so precisely engineered for influence that surrender feels like freedom.
This isn't hyperbole. It's documented in patents most users will never read, including Apple's US20230225659A1 for analyzing brain waves through AirPods, and US Patent 6,506,148 B2 describing nervous system manipulation through electromagnetic fields from screens. The same principles Dr. Ewen Cameron used to wipe memories at McGill University now operate through devices we pay monthly to use—updated bi-weekly with new features designed to deepen the neural pathways of dependency.
The same dissociation documented in MKULTRA Subproject 136 now manifests as digital amnesia, scrolling endlessly while forgetting why you started. The handler techniques that once managed Monroe's behavior now operate through automated content algorithms—no physical handlers required when the device itself becomes the relationship manager.
From The Laboratory trauma chambers to The Theater spotlights to The Network notification pings, the control grid tightens. Once classified MKULTRA experiments that evolved through Hollywood's theater of influence have become consumer products we line up to buy. The Network transforms mind control from a covert operation into a subscription service—The Laboratory's methods and The Theater's scripts deployed through palm-sized digital companions we eagerly upgrade every two years.
•••
Mass Trauma Events: When Mind Control Went Mainstream
“Before algorithms took over the job of influencing our thoughts, mass trauma events served as society-wide ‘pattern interrupts’—creating the same kinds of dissociative states in entire populations that MKULTRA tried to induce in individual subjects.”
The Network's earliest form operated through broadcasted trauma—leveraging mass media to create collective psychological states primed for manipulation. Before algorithms took over the job of influencing our thoughts, mass trauma events served as society-wide ‘pattern interrupts’—creating the same kinds of dissociative states in entire populations that MKULTRA tried to induce in individual subjects. These weren't random tragedies but strategic breakpoints in collective consciousness—functioning effectively as psychological reset buttons that recalibrated public perception on a global scale. As we'll see in the cases that follow, these broadcast events fundamentally altered how billions of people processed information and formed reality
These sequential trauma events represent what could be called a ‘field shock cascade’—each reset calibrated to coincide with specific technological expansions and shifts in collective perception. Every shock creates the neurological conditions for new control mechanisms to be accepted, while simultaneously fragmenting shared reality into increasingly polarized perceptual domains. This isn't merely chronological coincidence but a functional pattern: societal trauma followed by accelerated technological integration, followed by normalized surveillance, followed by deeper reality divergence.
The OJ Simpson Trial: The Network's First Captive Audience
The 1994-1995 OJ Simpson trial represents the moment when The Network graduated from experimental phase to operational deployment. After the brutal murders of Nicole Brown Simpson and Ronald Goldman, the subsequent manhunt, trial, and acquittal of football legend O.J. Simpson became America's first mass-scale exercise in collective attention capture—establishing the template for what would later become algorithmic addiction. This wasn't just a murder trial—it was the first deliberate spectacle that demonstrated how effectively the media could command consciousness at population scale.
For youngsters who might not remember or understand, OJ Simpson wasn't just an athlete—he was American royalty. Star football player turned actor, sports commentator, and commercial pitchman, his crossover appeal made him one of the most recognized faces in America. When the white Bronco chase interrupted prime-time programming on June 17, 1994, 95 million viewers—more than half the country—watched transfixed as helicopters followed the slow-motion pursuit down the 405. For my generation, it became our "Where were you when..." moment, at least for the next seven years.
The chase marked a turning point. Twenty-four hour news networks were still relatively new—CNN had pioneered the format only in 1980—and the World Wide Web was just starting to gain mainstream adoption. This convergence of technologies demonstrated their true power: not just delivering information, but commanding mass consciousness. America wasn't just watching the chase; we were participating in it, creating the first real-time, nationwide shared psychological experience of the digital age.
This moment marked the critical inflection point for mass media. Talk shows were simultaneously transforming—shifting from Oprah's therapeutic confessional style to Jerry Springer's orchestrated chaos. Jenny Jones and Ricki Lake trained viewers to see themselves as potential stars of their own dramas, while Maury Povich made confrontation the main attraction. The first reality TV shows like MTV's The Real World and Road Rules were teaching audiences to embrace voyeurism as entertainment—ordinary people becoming celebrities simply by living dramatically on camera. As Warhol predicted, everyone would get their 15 minutes of fame*—what looked like entertainment evolution was actually systematic neural reconditioning—with media systems optimizing to produce authentic-seeming drama that viewers both consumed and performed.
*Like many artists of the 1960s, there is ongoing speculation that Andy Warhol had ties to CIA cultural initiatives, given the agency’s documented role in promoting modern art during the Cold War. His Factory attracted a wide range of cultural figures, some loosely linked to CIA-funded programs, reflecting the era’s blurred lines between art and politics. His art explored themes of repetition and psychological programming. But that's another rabbit hole entirely.
From that June night through the verdict announcement 16 months later, the trial commanded non-stop coverage across all major networks. Day after day, gavel-to-gavel television transformed legal proceedings into must-see TV.
Meanwhile, the Advisory Committee on Human Radiation Experiments quietly released their report documenting decades of unethical experiments conducted on American citizens—including institutionalized children and pregnant women subjected to radiation testing without consent. This bombshell, revealing methods parallel to MKULTRA's psychological experiments, received merely 30 minutes of coverage across all networks combined. This stark contrast demonstrates The Network's deliberate curation of public awareness—choosing which stories deserve non-stop coverage and which revelations should remain practically invisible despite their significance.
When the verdict finally arrived on October 3, 1995, over 100 million viewers watched live—creating not resolution but deeper fracture. The split-screen images of celebrations in black communities and stunned silence in white ones revealed something far beyond a legal decision. Two Americas had been watching entirely different trials, constructing parallel realities from the same evidence—a pattern of perception fragmentation that would repeat consistently across domains in subsequent decades.
This wasn't merely divided opinion but divided perception itself—the same pattern of reality fragmentation that laboratory experiments achieved in individuals now scaled to entire demographics. What looked like disagreement over facts was actually the creation of incompatible 'reality tunnels' where certain thoughts became literally unthinkable depending on which perceptual environment you inhabited. This blueprint for reality division would later be perfected through personalized news feeds, with algorithms tailoring content not just to inform but to shape what feels possible to think.
This timing demonstrates how The Network operates through two key functions:
Attention Capture: The trial created the prototype for continuous engagement that social media would later perfect. Simple water cooler debates and call-in shows evolved into 24/7 news cycles and eventually algorithmic feeds. Viewers weren't merely watching - they were emotionally invested, developing parasocial relationships with figures they'd never met, and sacrificing unprecedented amounts of mental bandwidth to a manufactured narrative. This transformation from passive viewing to active psychological participation established the neurological pathways that would later make smartphone addiction possible.
Division Engineering: The trial amplified racial fractures through competing narratives precisely calibrated to trigger different responses in different demographics. When the verdict split largely along racial lines, it created two distinct realities—one celebrating justice, another decrying injustice—the exact same perceptual divergence that would later be automated through personalized news feeds and recommendation algorithms. This wasn't just divided opinion; it was divided reality - the first mass demonstration of what would become The Network's core function.
If I actually believe what I wrote in Part 2 about The Theater's methods, then I must at least consider the possibility that an event of this cultural magnitude contains more than meets the eye. Part of pattern recognition is allowing yourself to consider an idea without necessarily believing it. Several unexpected biographical connections emerge that, while not proving direct involvement, create an unusual network of institutional intersections:
Simpson's mother worked at UCSF Medical Center, an institution with documented MK ULTRA ties at the time
His father was a Federal Reserve employee who lived openly as a transvestite in the 1970s—unusual for the era and perhaps noteworthy
Former CIA Director William Colby's son Carl lived next door to Nicole Brown Simpson—another fascinating coincidence; Carl's wife testified under the name "Miss Boe"—either her maiden name or an alias
Even Simpson's entertainment career created an eerily prescient connection. In The Naked Gun films, his character helps foil an assassination attempt by a mind-controlled athlete—a plot that directly references MKULTRA's Manchurian Candidate objectives. The irony of OJ Simpson playing a hero who stops programmed violence before allegedly becoming the perpetrator creates yet another curious serendipity.
The Simpson trial wasn't the only event of the 1990s that deepened social divisions. The pattern extends to the Rodney King beating, L.A. riots, Ruby Ridge, and Waco.
This same pattern extended into pop culture through precisely timed cinematic and media representations. The early 90s saw Black rage narratively packaged in films like Boyz n the Hood and Menace II Society, while gangsta rap from N.W.A. and Ice-T channeled urban frustration into marketable rebellion. Simultaneously, white alienation found its defining expression in Michael Douglas's Falling Down, where an ordinary man's violent breakdown became cultural shorthand for middle-class white male rage. This archetype gained political voice through Rush Limbaugh's explosive rise in talk radio, which grew from 100 stations in 1988 to more than 600 by 1995. Shows like Cops supposedly documented ‘reality’ while reinforcing existing perceptions—for some viewers confirming stereotypes of criminality, for others validating perceptions of systemic bias—effectively strengthening whichever narrative the viewer already favored.
These parallel narratives—urban collapse vs. rural resistance—fractured cultural identity along racial and ideological lines, deepening division through emotionally charged representation. This wasn't random cultural evolution; it was engineered schismogenesis—the systematic polarization of groups through cultural programming that I documented in previous essays. This term describes how social divisions are deliberately amplified by the creation of opposing cultural narratives that drive groups further apart. Hollywood and the music industry weren't just reflecting division—they were manufacturing it, creating the emotional templates The Network would later algorithmically refine into personalized hatred.
What appeared as organic cultural conflicts reveal remarkable consistency with engineered division, techniques now refined through algorithmic polarization.
The Network's First Live Test: Division By Design
The OJ phenomenon illuminates how The Network functions: not merely transmitting information but manufacturing engagement and division simultaneously. Here was the paradox: a nationwide shared experience that produced completely divergent interpretations. The same evidence, watched by millions together, somehow created incompatible realities—demonstrating how mass media could be used not just to connect, but to fundamentally shatter collective understanding. A template that would evolve from broadcast television to algorithmic personalization, achieving the same outcome: divide, capture, control.
While the Simpson trial demonstrated The Network's power to manufacture engagement and division, its origins lay in an earlier era of one-way programming. To understand how we arrived at participatory spectacle, we must return to the prototype: the JFK assassination.
The JFK Assassination: Broadcasting Trauma as a Reset Button
This wasn't just a presidential assassination—it was the ritual sacrifice of a beloved symbol of American optimism in broad daylight. They could have poisoned President Kennedy if mere death was the objective; instead, they murdered him publicly, like the killing of a sun god—a ceremonial destruction of hope performed for maximum psychological impact. As my mother recently told me, even her high school prom months later was canceled—the cultural depression was that consequential.
The famous "where were you when..." question that I mentioned earlier with the OJ Simpson case still echoes decades later reveals how deeply this event imprinted on the collective psyche. The hopeful spirit of the early 60s was replaced by a darker, more cynical worldview, creating psychological conditions that made the escalation in Vietnam more acceptable. The effect wasn't just political—it was a fundamental rewiring of America's psychological landscape.
The template set by JFK’s assassination evolved into something more systematic. No longer content with isolated shocks, The Network developed ongoing narratives of fear that could maintain populations in a permanent state of suggestibility.
Wars Without End: Perpetual Fear as Control Mechanism
This pattern of manufactured crises extends beyond isolated events to entire societal narratives. We've witnessed a telling progression from The War on Drugs to The War on Terror to The War on Covid to The War on Climate. Each of these campaigns follows a consistent template: identify a threat that generates primal fear, position authorities as the sole protectors, and implement control measures that would be rejected under normal circumstances. While presented as necessary safeguards, these "wars" function as systems of unrestricted psychological warfare aimed at control rather than resolution. They represent the gradual normalization of surveillance and restriction—the same methodologies developed in MKULTRA but deployed at societal scale.
While adults navigated these perpetual wars on abstractions, The Network found children to be its most malleable subjects. The Challenger disaster became a defining psychological event for this vulnerable population.
The Challenger Disaster: Programming Children's Consciousness
The Challenger explosion targeted children's developing psychology. I vividly remember watching this in school, as did millions of other children across America. NASA's heavily promoted "Teacher in Space" program ensured maximum childhood viewership. In my previous essay Space, Symbols, and Suspicion, I explored something that typically provokes immediate eye-rolls from friends and family: several Challenger astronauts appear to have doppelgängers with identical names who continued public lives decades later. However, when I show those friends the actual visual evidence, not one can provide a reasonable explanation for these statistical impossibilities.
When viewed through a pattern recognition lens, events like Challenger serve multiple functions in a mind control framework: creating collective trauma, establishing boundaries of acceptable inquiry, and potentially serving as cover for operational continuity. I won't relitigate the full evidence here—that's available in my previous work—but the mathematical improbability of these identity correspondences reveals pattern signatures that transcend coincidence. The Challenger Disaster and other such events serve as society-wide ‘breaks in consciousness’ that facilitate major shifts in perception and policy. Could this collective childhood trauma have served to redirect questions about space exploration priorities, establishing boundaries of acceptable inquiry just as a generation was forming its worldview?
The 9/11 Attacks: Mass Reprogramming and Surveillance Acceptance
The 9/11 attacks enabled the most comprehensive mass reprogramming in modern history. Beyond the immediate trauma, September 11th justified two decades of warfare based on demonstrably false pretenses, massive taxpayer fund transfers to private military contractors, and unprecedented domestic surveillance. The Patriot Act, absurd airport security theater, and the normalization of constant monitoring all stemmed from this single event. Within hours, policies and powers that would have faced fierce resistance before were suddenly accepted as necessary safeguards.
The constant replay of the towers falling created a field effect where questioning the subsequent war on terror felt unpatriotic or insensitive. This wasn't achieved through direct censorship but by engineering an emotional environment where certain thoughts felt inappropriate or taboo. The media's repetition of the traumatic imagery established perceptual boundaries around what could be publicly discussed.
Even today, nearly a quarter-century later, the perceptual boundaries established by this trauma remain largely intact. Many people still experience visceral discomfort at questioning any aspect of the official narrative—not because they've examined contradictory evidence and rejected it, but because the very act of questioning feels wrong on a pre-cognitive level. This demonstrates the lasting power of field effects in shaping what thoughts feel possible or permissible long after the initial programming event.
This discomfort extends beyond specific events to a deeper cognitive barrier—the very idea that one's own government—or other powerful force—might deliberately orchestrate or permit such tragedies creates a psychological short circuit that most people find too destabilizing to entertain. It's not merely about evaluating evidence but confronting a possibility that threatens the fundamental trust structure of modern society.
COVID-19: Engineering Divergent Realities
Two decades after 911 transformed airline travel and normalized domestic surveillance, the COVID-19 phenomenon demonstrates perhaps the most sophisticated application of reality engineering to date. Populations experienced not merely disagreement about facts but entirely different perceptual frameworks—divergent realities operating in parallel. Digital technology accelerated this fragmentation, creating the illusion of togetherness while physically isolating people in their homes, each consuming personalized reality streams.
The perceptual division continues today in visible daily patterns: some still wear masks while others act as if the pandemic never happened; remote work has become normalized for some professions while others insist on physical presence; and an entire generation of children now understands "socializing" as potentially meaning digital interaction rather than physical proximity. Beyond these behavioral markers lies something more remarkable: entire epistemological systems diverged, with different segments of the population inhabiting increasingly separate information ecosystems that render certain thoughts unthinkable within their respective reality tunnels.
This wasn't merely polarization but perception management at scale—the culmination of mind influence techniques applied at population level, where shared reality itself fragments into programmable alternatives. The Network's most sophisticated achievement wasn't just influencing what people thought about specific interventions, but creating parallel perceptual environments where the basic frameworks for determining truth versus falsehood themselves diverged.
•••
Mass Ritual Programming: The Spectacle Network
While these mass trauma events served as pattern interrupts, The Network maintained control between them through cyclical rituals that synchronized consciousness at scale. The principle isn't new—as we saw with the Grateful Dead's chemically—enhanced concert experiences in Part 2: The Theater, collective synchronization of emotional and perceptual states creates powerful opportunities for programming. What's changed is the scale— from thousands of Deadheads in concert venues to billions of viewers worldwide watching identical spectacles simultaneously.
These aren't just spectacles but operational templates for consciousness management—each ceremony encoding specific archetypal patterns that bypass critical thinking and resonate directly with collective unconscious structures. The power lies not just in what is seen, but in how these symbols activate ancient recognition pathways while delivering entirely modern programming directives.
Between these trauma-based resets, The Network maintains control through cyclical mass rituals that capture collective attention and synchronize emotional states. In an interconnected world, these function as "bread and circuses" but at internet scale—simultaneously distracting and conditioning billions of minds through shared spectacle.
Olympic ceremonies stand as the most elaborate of these global rituals. The 1992 Barcelona ceremony included a massive virus-like structure alongside mythological symbolism.
The 2012 London opening ceremony took this further with hospital beds, dancing nurses, and a giant figure resembling a viral cell—imagery that seemed oddly prescient years later during the COVID pandemic.
Most recently, the 2024 Paris ceremonies sparked international controversy with a tableau featuring drag performers and transgender entertainers in a scene many interpreted as deliberately mocking Leonardo da Vinci's Last Supper. This juxtaposition of transgender representation with sacred Christian imagery created precisely the kind of cultural division we've seen engineered through other events - pitting religious conservatives against progressive advocates in yet another manufactured cultural battle. By combining two of society's most contentious issues (gender identity and religious tradition) in a single provocative display, the ceremony functioned as another example of engineered schismogenesis - deepening social fractures through orchestrated spectacle.
Even memorial services incorporate these patterns. The 9/11 memorial ceremony featured performers arranged in the distinct shape of the Eye of Horus—an ancient Egyptian symbol of protection and royal power—visible only from aerial camera angles. This integration of ancient symbolism into modern events creates resonance beyond conscious awareness, operating at the level of archetypal recognition.
Super Bowl halftime shows function similarly, with performances carefully designed to create mass hypnotic states. The synchronized experience of millions watching identical imagery while experiencing the same emotional peaks creates neurological conditions similar to those we explored with the Grateful Dead phenomenon—only now scaled to hundreds of millions. I could share hundreds of examples across decades of performances.
Analysts like Jay Dyer and Jamie Hanshaw have offered compelling interpretations of these spectacles, revealing their ritualistic underpinnings. Madonna's 2012 performance transformed the field into an Egyptian temple with hieroglyphic patterns and goddess worship imagery, while Katy Perry's 2015 show featured mechanical beasts, chess-board patterns representing duality, and cosmic symbolism. These aren't random aesthetic choices but carefully orchestrated visual languages that operate at an archetypal level.
The same pattern manifests in ceremonies like the 2016 Gotthard Tunnel opening in Switzerland, where European leaders watched performers in goat-headed costumes enact death and rebirth symbolism.
The 2021 Astroworld concert provides another striking example, where Travis Scott performed on a stage designed as a portal while ten attendees lost their lives. Whether staged as entertainment, infrastructure celebration, or memorial service, these mass rituals create the perfect conditions for collective consciousness programming.
Left: Travis Scott Astroworld Concert // Right: Medieval "Mouth of Hell" painting (Bosch school)
What makes these rituals particularly effective is their networked distribution. Unlike previous eras where spectacles remained local, today's global broadcasts create simultaneous conditioning across billions of minds. The Network allows these rituals to function not merely as entertainment but as consciousness programming operating through archetypal imagery and emotional synchronization. From ancient amphitheaters to today's globally streamed spectacles, these rituals have always served multiple purposes: entertainment for the masses, yes, but also reinforcement of cultural narratives and—increasingly—testing grounds for new perception management techniques.
These mass rituals create the perfect bridge between individual dissociation and technological entrainment—the synchronization of brainwaves or biological rhythms to external stimuli. They establish the psychological conditions necessary for large-scale programming while simultaneously serving as vehicles for introducing symbolic content that shapes cultural narratives. This isn't about hidden conspiracies but observable functions—the same techniques documented in MKULTRA research, now deployed through cultural channels with billions of voluntary participants.
•••
WEF: Institutional Normalization of Mind Control
"Humans are now hackable animals. The whole idea that humans have this soul or spirit, and they have free will, and nobody knows what's happening inside me, so whatever I choose, whether in the election or whether in the supermarket, this is my free will—that's over."
These aren't the words of a conspiracy theorist or science fiction author. This is World Economic Forum (WEF) advisor Yuval Noah Harari openly declaring what The Network has achieved. The same institution that shapes global policy now normalizes technologies that would have horrified the public when MKULTRA was exposed.
The WEF represents the perfect embodiment of the public-private partnership model that dominates contemporary power structures. While lacking formal governing authority, its annual Davos meeting brings together over 1,000 corporate partners, 100 governments, and major international organizations under the guise of "improving the state of the world." This is where CEOs who control our digital ecosystems meet with heads of state who control legislation—a strategic convergence of interests that WEF founder Klaus Schwab famously described as the "penetration of cabinets." This coordination between corporate and state power echoes elements of corporatism—the economic system Mussolini established as a component of fascist governance.
In November 2018, the WEF published an article titled “Mind control using sound waves? We ask a scientist how it works" on their official website. The article featured University of Oxford Professor Antoine Jérusalem discussing non-invasive brain stimulation using ultrasound technology. He explicitly confirms: "Ultrasound neuromodulation is something that definitely works, but that we still don't understand." More disturbingly, he acknowledges that "since the brain is the de facto centre of decision for so many processes, any of them could be targeted." This public acknowledgment marks a stunning shift from covert research to open advocacy. The casual language of 'targeting' brain processes reveals the underlying perspective—while presented as advancing medical science, the framing suggests applications focused on directive control rather than healing.
The institutional integration runs deeper than rhetoric. At the 2023 Davos panel Ready for Brain Transparency? Dr. Nita Farahany demonstrated real-time brain decoding using simple wearable devices: "We can pick up and decode faces that you're seeing in your mind—simple shapes, numbers, your PIN number to your bank account." This wasn't speculative futurism but operational technology being demonstrated to the world's most powerful decision-makers.
What makes this particularly chilling is the acceleration timeline. Gary Marcus, cognitive scientist at the 2024 Mind and the Machine panel, warned these technologies function as "Trojan horses"—seemingly innocuous devices that collect neural data while providing other services. While experts debate exact timelines, there's consensus that AI integration has dramatically shortened development cycles. As UN Technology Envoy Amandeep Singh Gill noted, "You are able to process signals in a significantly different way" due to AI's pattern-recognition capabilities.
The real-world implementation is already well underway. More than 5,000 companies worldwide monitor employees' brainwaves for fatigue levels. Train conductors on the Beijing-Shanghai line wear brain-scanning hats as a condition of employment. Technologies originally developed in classified intelligence programs are now standard workplace practice, with the backing of the world's most influential institutions.
Martin Fussenegger's 2016 WEF presentation on Mind-Controlled Therapeutics demonstrates the integration pathway. His technology uses headsets to record brain waves that control implants delivering drugs based on mental commands—a direct evolution of what MKULTRA researchers could only dream of achieving. "Eventually, we go towards a world of therapeutic thinking, and we can intentionally control transgene expression in our body," he explains, as WEF positions this capability as medical innovation rather than unprecedented neural colonization.
The WEF's "Final Frontier" agenda treats the brain as simply another territory to conquer. Through strategic partnerships with neural technology companies—including Synchron for "non-invasive neural interfaces" and Microsoft/Accenture for metaverse platforms incorporating neural tech—the WEF ensures implementation pathways for technologies that originated in military research.
Compare the CIA's 1952 ARTICHOKE Memo asking "Can we get control of an individual to the point where he will do our bidding against his will?" with Klaus Schwab's vision of "fusion of our physical, digital, and biological identities." Only the branding has changed. What was once classified research has now become openly acknowledged programming, with the full weight of global institutional convergence behind it.
"Compare the CIA's 1952 ARTICHOKE Memo asking 'Can we get control of an individual to the point where he will do our bidding against his will?' with Klaus Schwab's vision of 'fusion of our physical, digital, and biological identities.' Only the branding has changed."
The WEF's normalization of mind influence technology represents the perfect bridge between laboratory research and mass implementation. It demonstrates how the tools of psychological manipulation move through a predictable pipeline: from DARPA funding to corporate development to institutional endorsement to global deployment—all while being reframed from "mind control" to "cognitive augmentation" and "brain transparency."
This institutional blessing ensures not just acceptance but eager adoption of technologies that fundamentally threaten cognitive sovereignty. When the architects of global policy openly advocate for "brain transparency," we're witnessing the final phase before universal implementation—the moment when mind control completes its journey from the shadows of classified research to the spotlight of celebrated innovation.
•••
Navigating the Technical Section
If you're still with me after all we've uncovered, here's where things get a bit technical. I know patent numbers can make eyes glaze over, but these aren't just bureaucratic documents—they're receipts for the massive technological evolution that transformed mind control from classified experiments into the devices we carry daily.
What follows may feel like wading through technical specifications, but these patents document the actual methods for influencing thought, emotion, and behavior through consumer technology. Think of them as the paper trail for the mind control shopping spree that's been happening while we were distracted by cat videos.
While I've included comprehensive technical documentation to establish a factual foundation, the key takeaway is the pattern these patents collectively reveal—the gradual development of technologies capable of influencing human consciousness. The specific patent numbers matter less than their demonstrated capabilities and progression over time.
Feel free to skim this section if you're primarily interested in the narrative flow and focus on the real-world examples provided. That said, the sheer volume of documented technologies itself tells a story—what seemed like science fiction in MKULTRA's era has become shopping mall reality. The methodical presentation mirrors pattern recognition analysis: individually, each patent might be dismissed; collectively, they reveal systematic development of consciousness manipulation tools.
For the tech enthusiasts among you—I've attempted to balance technical accuracy with accessibility. Any errors in interpretation are mine alone in trying to make complex neurotechnology comprehensible to general readers.
Patent Documentation: The Blueprint for Neural Colonization
"We have the technology to hack human beings on a massive scale," Harari warned at the WEF’s 2020 conference in Davos. He was not bluffing: this technology is publicly documented in thousands of government patents, hiding in plain sight for anyone who cares to look.
"It is therefore possible to manipulate the nervous system of a subject by pulsing images displayed on a nearby computer monitor or TV set." - US Patent 6,506,148 B2
Picture this: You're watching a video when suddenly, you feel inexplicably anxious. Your heart rate increases, your muscles tense. Is it the content, or something more insidious? US Patent 6,506,148 B2, filed by Hendrikus G. Loos in 2003, may provide the answer: "Nervous System Manipulation by Electromagnetic Fields from Monitors." The patent explicitly describes: "It is therefore possible to manipulate the nervous system of a subject by pulsing images displayed on a nearby computer monitor or TV set." Not science fiction—patented technology capable of inducing physical responses through standard screens.
The patent trail reveals a technological lineage from crude MKULTRA experiments to today's sophisticated neural interfaces. Each document represents another piece of the cognitive sovereignty puzzle being slowly disassembled:
Information Extraction Technologies
Imagine a device that reads your thoughts as easily as a barcode scanner reads prices. US Patent 6,011,991 (2000) for brain wave analysis shows the same pattern of mind reading that MKULTRA researchers pursued with electrodes and drugs—transforming private thoughts into data for external access.
This builds on US Patent 3,951,134 (1976) for "Apparatus and Method for Remotely Monitoring and Altering Brain Waves," demonstrating how early military technology evolved into consumer applications.
This technology transforms the most private domain—your own mind—into readable data. The implications extend far beyond medical applications to potential monitoring, interrogation, and even thought prediction.
Behavior Modification Systems
Beyond monitoring, these patents detail active influence. US Patent US2016/0375220A1 (2016) for magnetic brain modulation reveals the same pattern as electroshock treatments in classified experiments—changing thought patterns through external signals. What once required invasive procedures now happens wirelessly, but the architectural signature of controlling minds from outside remains identical.
Loos's monitor manipulation patent (#6,506,148) specifically notes that "certain monitors can emit electromagnetic field pulses that excite a sensory resonance in a nearby subject, through image pulses that are so weak as to be subliminal."
Consumer Integration
The most concerning development is the seamless migration of this technology into everyday product development. Apple Patent US20230225659A1 (2023) for monitoring—yes, monitoring—brain waves through AirPods shows the same pattern we saw in MKULTRA—accessing people's thoughts without their consent, awareness, or full understanding. Methods pioneered in classified labs are now being patented for sleek packaging at the Apple Store, with users potentially soon paying for the same brain monitoring that once required secret government programs.
This represents an industry-wide trajectory toward neural monitoring. In an interview with Theo Von released just this week, Meta CEO Mark Zuckerberg said "the perfect form factor for a device where if you want to have an AI that you let see what you see, hear what you hear, it can talk to you, you can talk to it throughout the day"—precisely the kind of persistent neural companion that creates unprecedented access to consciousness.
In fact, Meta has already patented technology that aligns with this vision. Patent US20140198035A1 (2019) for "Wearable Muscle Interface Systems, Devices and Methods"—technology that captures electrical signals from users' muscles to control computing devices. By moving from brain waves to muscle signals, this represents another vector of physiological data capture being normalized through consumer technology.
Even individual inventors are developing such technologies, as seen in Patent US20150045007A1 (2014) by Duane Matthew Cash for a "Mind-Controlled virtual assistant on a smartphone device"—explicit bidirectional interface between brain and phone. This widespread development across major corporations and independent inventors demonstrates how thoroughly neural interface technology has penetrated the innovation ecosystem.
This represents the path from classified research to consumer adoption—no coercion needed when users pay for their own neural interfaces.
The progression is clear: from influencing our biology externally through light frequencies to monitoring our neural activity directly through ubiquitous consumer devices. The same mechanisms that create addiction loops through dopamine manipulation are now being enhanced to read—and potentially write to—our neural circuitry directly.
What does all this mean in human terms? Imagine a teen, her earbuds tracking neural patterns as TikTok feeds shape her desires—a closed-loop system molding her thoughts without her awareness. This isn't science fiction but the logical application of technologies documented in patent filings. The pattern is clear: each patent extends deeper into our cognitive architecture, each consumer product brings surveillance closer to our neural activity, each interface makes external influence more seamless and less detectable.
Technologies once requiring dedicated equipment and controlled environments now operate through devices billions carry with them everywhere daily. This isn't speculative futurism. As I documented extensively in my essay Node Without Consent: The Battle Against 6G and the Internet of Bodies, these human-as-network technologies are explicitly part of next-generation wireless development plans. Industry pioneers like Josep Miquel Jornet openly envision a world where "your body's cells [are] connected to the internet," while IEEE standards committees have already created protocols (802.15.6) specifically designed for "Wireless Body Area Networks." The technological architecture for 6G isn't just about faster phones—it's about integrating human biology directly into the digital infrastructure, turning your cells into networked data points whether you consent or not. This biodigital convergence represents the next phase in mind control's evolution: from influencing your thoughts through external stimuli to directly networking your neurons into systems designed for bidirectional data flow.
The extensive catalog of mind influence technologies spans multiple decades, with Appendix A documenting dozens of patents ranging from early behavior modification techniques to modern neural interfaces. My exploration of these patents was initially inspired by inimitable researcher RedPill Drifter's comprehensive documentation of these technologies.
Technologies developed in underground MKULTRA laboratories now hide in the small print of user agreements we accept without reading. The Laboratory created the methods, The Theater normalized them, and now The Network delivers them through devices we eagerly upgrade every upgrade cycle. The—patents noted above - and many others - aren't merely technical specifications gathering dust in government archives—they represent the blueprint revealing the same control pattern across decades.
From classified mind control experiments to consumer products, the blueprint remains consistent: access consciousness without consent, shape behavior without awareness, and collect data without understanding. The pattern is consistent with the evolution described throughout this series: from visible to invisible, from coercive to voluntary, from specialized to ubiquitous. Just as Edison's explicit film monopoly evolved into subtle algorithmic control, mind influence technologies have progressed from crude electroshock to elegant consumer electronics.
•••
The Military-Industrial Pipeline: From Classified Weapons to Consumer Products
Throughout modern history, military research programs have consistently served as incubators for technologies that eventually reach consumer markets. What emerges from classified defense laboratories inevitably finds its way into everyday devices, creating a predictable pipeline from military innovation to commercial application. This pattern—from Pentagon labs to living rooms—reveals one of The Network's most concerning aspects: technologies developed for warfare are rebranded as convenience, health, or entertainment. The evolution from specialized psychological operations to ubiquitous consumer technology follows a consistent architectural signature that suggests systematic rather than merely accidental development.
"Voice of God" Weapons
Among the most advanced publicly acknowledged mind influence technologies are directional audio systems originally developed for military combat and crowd control. These systems, emerging from classified military research, represent the technological realization of what MKULTRA researchers could only attempt through cruder methods of psychological manipulation.
The LRAD (Long Range Acoustic Device) system, developed by American engineer Woody Norris, demonstrates the foundational technology. While primarily marketed as a communication and crowd control tool, Norris has openly described more sophisticated applications: "We can put a single sound right in one person's head. You could whisper in someone's ear from 100 yards away."
This capability was confirmed in Norris's TED Talk,, where he revealed how the military had deployed these devices in Iraq to create phantom troop movements or to target individuals with specific audio messages that only they could hear. He stated that the military was purchasing these $70,000 devices "as fast as we can make them."
Major news outlets like El País have reported on these "whispering beams" as technology that "sends sound to a specific person without the surrounding people hearing it," noting they could be used "for military purposes."
Military documents confirm the deployment of more advanced versions. A declassified military review references "voice-to-skull" devices (designated as V2K) capable of creating the perception of voices that only the targeted individual can hear. These systems operate by using microwave frequencies to create thermoacoustic pressure waves directly within the skull.
US Patent 5159703A, granted in 1992 for a "Silent subliminal presentation system," further documents this technological evolution. The patent describes methods for transmitting inaudible messages that can be detected by the human brain without conscious awareness—technology that aligns precisely with voice-to-skull capabilities. This represents another documented example of the same pattern: technology designed to access consciousness without consent or awareness.
The technology has evolved significantly since its early development. Advanced directional audio systems now employ ultrasonic carrier waves modulated with audio signals. When these waves interact with air, they demodulate and create audible sound only at specific focal points, allowing for extreme targeting precision.
Beyond simple audio projection, these technologies can potentially create more complex effects. Research has shown that specific sound patterns can induce altered states of consciousness, trigger emotional responses, or even implant suggestions that bypass normal critical faculties.
The implications for behavior modification are significant. A person subjected to voices they believe are coming from within their own head may interpret them as internal thoughts, divine guidance, or symptoms of mental illness—all interpretations that mask the external technological source of the experience.
Both "Voice of God" technology and HAARP reveal the same pattern signature: targeted frequency manipulation designed to override individual consciousness. Whether through directional sound that creates voices in your head or ionospheric disturbances that potentially affect mass behavior, the architectural design remains identical—external control through invisible frequencies that subjects rarely detect or understand.
The most compelling aspect of these technologies isn't necessarily their documented capabilities but how they operate in a deliberately maintained gray area—visible enough to establish their existence but sufficiently obscured to prevent comprehensive public understanding.
HAARP: From Military Ionospheric Research to Global Frequency Manipulation
The High-frequency Active Auroral Research Program (HAARP), a joint project of the U.S. Air Force and Navy officially described as an ionospheric research facility, demonstrates the potential for large-scale frequency manipulation. Patents associated with HAARP technology (particularly US Patent 4,686,605 by Bernard Eastlund) describe capabilities for "altering a region in the earth's atmosphere" through electromagnetic manipulation.
Even prominent figures have noted unusual atmospheric phenomena and their behavioral effects. In a remarkable television interview, the late great musician Prince observed: “This phenomena of chemtrails... when I was a kid, I used to see these trails in the sky all the time... And then you started to see a whole bunch of them. And the next thing you know, everybody in your neighborhood was fighting and arguing, and you didn't know why.” This peculiar observation from an unexpected source adds another pattern data point - someone with no stake in conspiracy theories simply reporting what they noticed.
A 1999 European Parliament report (Document A4-0005/99) expressed explicit concern that HAARP's electromagnetic capabilities could potentially "manipulate human behavior" and impact health on a large scale. The report called for an international independent body to assess HAARP, warning that it could "have a manipulative effect on human beings" through ionospheric modification. And yet most citizens remain completely unaware of HAARP's existence or capabilities.
Blue Light Protocols: From MKULTRA Experiments to Every Screen
The evolution of mind control reached everyday screens through discoveries made in military-funded laboratories. Dr. Jack Kruse, a neurosurgeon who has extensively researched electromagnetic frequencies, documents how MKULTRA researchers discovered that certain light wavelengths could alter brain function without physical implants.
"They found through the programs that the government sponsored at Tulane Neurosurgery and Neurology—called MKUltra—that they were able to control people through light waves," Kruse notes. While I'm not a neuroscience expert, Dr. Kruse most certainly is. His analysis shows how specific blue light wavelengths affect not just melatonin production but potentially neural signaling pathways directly. Every smartphone, computer monitor, and LED screen now emits blue light at frequencies documented to suppress melatonin and alter dopamine levels.
For those interested in a deeper exploration of these concepts, Dr. Kruse discusses the connections between electromagnetic frequencies and neural manipulation in this discussion about MK-Ultra and targeted frequency technologies:
As Kruse observes, "Why does every computer have a blue light screen? Why doesn't it come preloaded with f.lux or iris? Because the blue light lowers your dopamine and melatonin level so that you become addicted." The biological effects he documents align precisely with the behavior modification goals found in mind control research.
These effects create subtle but powerful forms of behavioral modification through addiction loops that mirror MKULTRA's control objectives, but implemented through voluntary consumer technology rather than covert operations.
DARPA's Neural Arms Race: Weapons Systems as Medical Miracles
The direct line from MKULTRA to present-day neurotechnology is most visible in DARPA's openly announced programs. The Neural Engineering System Design (NESD) program explicitly aims to develop "high-resolution, bidirectional brain-machine interfaces" capable of recording from and stimulating up to one million neurons.
Their SUBNETS program (Systems-Based Neurotechnology for Emerging Therapies) focuses on implanted devices that monitor and regulate brain activity to treat neuropsychiatric disorders—effectively creating the capability to modulate mood, behavior, and cognition through direct neural stimulation.
What distinguishes these contemporary programs is their public relations framework. Where MKULTRA operated covertly, today's neurotechnology research is presented as medical advancement and national security necessity. The Pentagon's Advanced Aerospace Threat Identification Program (AATIP) includes research into "psychotronic weapons" and "psychoenergetics"—modern terminology for technologies targeting consciousness directly.
This institutionalized continuation of mind influence research, now enhanced by AI systems, creates the potential for automated neural influence—algorithms determining when and how to modify human brain function without direct human oversight. The implications extend beyond therapeutic applications into cognitive warfare—a domain the military openly acknowledges as the future battlefield. As NATO's own 2020 Innovation Hub report explicitly stated: "The brain will be the battlefield of the 21st century" and "humans are the contested domain.
•••
The Digital Leash: Algorithmic Consciousness Capture
Dr. Ralph Greenson once managed Marilyn Monroe's entire life—controlling her schedule, medications, relationships, and career decisions. Today, that same level of control operates through the device in your pocket. No human handler required.
From Harley Pasternak to Algorithmic Control
The shift from personal handlers to device-based control represents mind influence technology's most elegant evolution. Where celebrity handlers like Harley Pasternak allegedly threatened Kanye West with institutionalization, today's algorithms perform this same function for billions simultaneously—accomplishing compliance more subtly but using identical psychological principles at unprecedented scale.
Former Facebook product manager Frances Haugen revealed how platform algorithms are engineered specifically to maximize engagement through emotional manipulation, noting that "anger and hate is the easiest way to grow on Facebook." Internal research showed algorithms creating dopamine addiction patterns—the same neural mechanisms targeted in MKULTRA's chemical experiments.
"Anger and hate is the easiest way to grow on Facebook."
- Frances Haugen, Former Facebook Product Manager
As Tim Kendall, former Director of Monetization at Facebook, admitted: "We took a page from the tobacco industry playbook... It's not an accident. It's a conscious choice. We were designing these products to be addictive."
The Handler in Your Pocket
The parallels to traditional handler-subject dynamics are unmistakable:
Intermittent Reinforcement: Like MKULTRA's variable reward schedules, social media employs randomized notifications and unpredictable engagement to create behavioral dependency
Emotional Triggering: Algorithms identify and amplify content that produces heightened emotional states, creating the suggestibility conditions handlers once induced through trauma
Reality Distortion: Personalized feeds create information bubbles more effective than the isolation techniques used in traditional programming
Behavioral Prediction: Shoshana Zuboff's "behavioral surplus" concept describes how data collection enables prediction and modification of future actions—surpassing anything MKULTRA researchers achieved manually
Mass Identity Engineering
These algorithmic systems don't just modify individual behavior—they reshape collective identity at unprecedented scale. CDC data reveals a striking pattern based on birth year: people born before 1995-96 (Millennials and older generations) show relatively stable transgender identification rates of around 0.3-0.4% for decades. Those born after this precise boundary (Generation Z) show a sudden, dramatic surge that continues climbing exponentially.
Chart Source
This birth year inflection point coincides exactly with when algorithmic social media became the primary socializing influence on adolescents. What changed wasn't human biology but the information environment shaping identity formation. While the graph shows the trend actually began with millennials at a modest 32-degree slope, it absolutely explodes with Generation Z at a near-vertical 78-degree trajectory. This dramatic acceleration defies any explanation based on natural evolution. This isn't merely propaganda at work—it's a fundamental restructuring of identity formation through technological mediation. While Millennials developed identity with partial social media influence, Generation Z developed almost entirely under algorithmic guidance—their formative years spent with TikTok and Instagram as identity architects. The unprecedented nature of this shift cannot be overstated—never before in human history has identity formation been so thoroughly mediated by technological systems designed specifically to influence behavior.
To be absolutely clear: I’m aware that gender dysphoria is a real psychological phenomenon. People who experience genuine dysphoria deserve compassion, appropriate care, and the dignity to live authentically. What demands questioning isn't the legitimacy of transgender experience but the statistical impossibility of such a sudden demographic shift emerging organically.
While algorithmic influence likely plays a significant role in this demographic shift, other potential factors shouldn't be overlooked—including the documented decline in testosterone levels across generations and the proliferation of endocrine-disrupting chemicals in our food, water, and consumer products. These environmental influences may be creating biological conditions that interact with social and technological factors. Nevertheless, the abruptness and magnitude of the change still suggests algorithmic amplification as a primary driver in what appears to be, at least partially, a socially influenced phenomenon.
In Part 2 we documented that the Tavistock Institute researched group dynamics and social control methods. Here, we find that same organization pioneering gender identity redefinition. Through its Gender Identity Development Service, Tavistock established itself as the epicenter of the gender dysphoria phenomenon. This represents yet another convergence point where the same institutions appear across multiple domains of consciousness manipulation—precisely the type of multi-vector signature that confirms architectural design rather than coincidence.
Attention Programming Cycles
This handler-subject relationship extends beyond identity formation into our broader awareness. The now-ubiquitous "NPC" meme (referring to non-player characters in video games who follow programmed scripts) captures the algorithmic programming cycle with disturbing accuracy: populations receiving periodic "updates" directing their attention and emotional energy toward specific causes in sequence—COVID, vaccines, Ukraine, Pride/gender identity, the middle east, and most recently, Elon Derangement Syndrome oscillating throughout as the consistent background programming.
Just as Monroe's handler dictated what she should care about, algorithms now direct what billions simultaneously focus on—cycling through causes with lockstep precision while creating the illusion of spontaneous mass concern. As I documented in The Couch Revolution, this system transforms genuine activism into performative gestures, creating what appears to be engagement while engineering ever-deeper passivity and dependency.
These algorithms don't just filter what you see—they shape what becomes thinkable in your personal world. Your information environment is curated by code designed to maximize digital engagement. This isn't censorship in the traditional sense; it's something far more effective. By controlling what information reaches you, these systems don't just determine what you know—they define the boundaries of what feels possible to think. The most powerful censorship isn't blocking information; it's making certain connections feel absurd or implausible within your personalized reality.
"Wouldn't we notice such manipulation?"
"If we're being programmed, why don't we feel it happening?"
"How could such pervasive control remain hidden?"
These objections overlook the central insight of this entire series: the most effective programming is precisely that which subjects don't recognize as programming. Just as fish don't notice water, those born into algorithmic immersion have no reference point for life without it. Those old enough to remember the pre-algorithmic world—like those who remember the OJ trial—are now a shrinking minority, their perspective increasingly dismissed as outdated. It doesn't take long to become submerged in this environment—even those who once knew a different world quickly adapt to the new normal. The mass addiction described in our opening section isn't recognized as abnormal because it has become normalized—the new baseline for human experience that no one can remember not experiencing.
Algorithmic Reality Tunnels: A Case Study in Divided Perception
These algorithmic reality tunnels—personalized perceptual environments created by social media algorithms that filter what information reaches us based on engagement patterns—aren't merely theoretical constructs—they're active forces shaping our daily interactions. I experienced this pattern firsthand in a recent exchange that perfectly illustrated how divided perceptions operate in real time.
After seeing someone I sort of know post on X, "No, seriously, fuck you. Stop with the holocaust inversion. It's perhaps the nastiest form of antisemitism" regarding comparisons between Gaza and the Holocaust, I shared an op-ed from Holocaust survivor and human rights activist, Vera Sharav. In it, Sharav declared, "Those who declare Holocaust analogies off-limits are betraying victims by denying the Holocaust's relevance." My intention wasn't to stake a position in this heated debate but to introduce nuance through the voice of someone with profound wisdom derived from her own personal journey.
What followed demonstrated the reality-splitting patterns we've examined throughout this essay. Despite directly referencing Sharav—an actual Holocaust survivor who explicitly supports making these comparisons—my conversation partner responded by asking: "Show me the Jews who are claiming that Israel is committing a 'holocaust' in Gaza?"
This question itself revealed the perception gap. I had literally just shared the work of a Holocaust survivor making this exact comparison, yet he asked the question as if no such person existed. Despite referencing Sharav's work three separate times throughout our exchange, he responded each time as if I hadn't mentioned her at all. It was as if Sharav was invisible to him—information that couldn't be processed within his reality frame.
I shared my own Jewish heritage (as progeny of Holocaust survivors with another grandfather who had been Menachem Begin's personal bodyguard) in an attempt to create a genuine human connection across our dividing perceptions. By revealing my personal relationship to this intergenerational trauma, I hoped to demonstrate that I understood the emotional weight of these issues while showing that even with this background, I had come to see beyond tribal boundaries. I wanted to illustrate how we might honor our heritage while still recognizing our shared humanity. Yet rather than engaging with this attempt at connection, he responded with a ChatGPT screenshot defining "Holocaust inversion" as antisemitism—effectively outsourcing his thinking to an algorithmic system to validate his pre-existing dogma.
This exchange wasn't merely disagreement—it represented two fundamentally incompatible perception systems operating in parallel. Like the divergent realities that emerged after the OJ Simpson verdict, we weren't simply disagreeing about facts but experiencing entirely different frameworks of what feels possible to think. The most revealing aspect was how strongly algorithmic bubbles protect themselves against contradictory information. When presented with evidence that directly challenged his entrenched worldview (a Holocaust survivor supporting exactly what he claimed almost no Jews support), my conversation partner couldn't integrate this information. Her existence itself couldn't penetrate his reality tunnel.
Eventually, I recognized we were caught in what I described to him as a "recursive loop—repeating the same pattern without reaching a resolution condition." It wasn't his fault—the algorithmic bubble wasn't something he chose consciously. It was a pattern I've observed countless times, including in myself. There's something deeply sad about watching someone's intellect trapped within invisible walls they can't perceive. This realization led to the only productive action: "I'm choosing to break the loop."
This small interaction illuminates something pervasive about our current information environment. Field effects created through personalized media don't just influence opinions—they shape what information we can even perceive and process.
This pattern echoes what we observed with the OJ Simpson trial, where identical evidence produced divergent interpretations along predictable lines. It also raises questions about the paradigm we discussed with Kanye West's statements—particularly considering his documented mental health struggles and relationship with Harley Pasternak, who as we've seen, displayed concerning handler-like behaviors. The timing between West's controversial statements in 2022 and the broader conversations that emerged after October 2023—specifically the surge in antisemitism discussions following the Israel-Gaza conflict— creates another potential data point in our pattern recognition framework. Without claiming definitive causality, we can observe these architectural similarities across seemingly unrelated domains.
The trauma-based programming techniques once developed in classified settings have evolved into algorithmic systems that fragment shared reality itself.
By recognizing these patterns as they unfold, we gain something essential: the ability to step outside predetermined responses. Pattern recognition isn't just analytical but practical—identifying these structures is the first step toward reclaiming conscious choice in a world designed to automate our thinking. When we name the pattern, we create the possibility of seeing it—and breaking it.
You're Not the User, You're the Subject
The device operates as a 24/7 handler, monitoring emotional states, predicting responses, and delivering precisely calibrated content to maintain optimal engagement. Unlike human handlers who required physical proximity, algorithmic handlers accompany subjects everywhere, learning from every interaction.
What MKULTRA achieved through crude intervention, digital systems now accomplish through sophisticated psychological manipulation delivered via interfaces we consult hundreds of times daily. The handler-subject relationship hasn't disappeared—it's been automated, democratized, and embedded in technology we purchase voluntarily.
This evolution is happening by design. In this week's Theo Von interview, Zuckerberg described Meta's "personal AI" development as technology that "gets to know you" and understands "what you think is funny" to better "relate to you." What was once the domain of human handlers manipulating celebrities is now being developed as consumer AI that builds intimate knowledge of users' psychological profiles—all packaged as helpful personalization rather than systematic influence.
The Perfect Integration
When combined with the frequency technologies and neural interfaces discussed earlier, algorithmic behavior modification creates unprecedented potential for mass influence. The smartphone isn't merely a communication device—it's the most sophisticated psychological control mechanism ever deployed, operating with users' enthusiastic consent.
As Harari warned, "We are now hackable animals." The device in your pocket proves his point. It's not just collecting data—it's managing your consciousness, one notification at a time.
•••
Mass Shooters: Network Operations of Programmed Violence?
When viewed through our pattern recognition framework, these seemingly isolated mass shooting incidents reveal convergent signatures that traditional analysis often misses. The same control architecture that functioned in laboratory settings—trigger phrases, dissociative states, amnesia barriers—appears consistently across cases that may seem unrelated to each other. This isn't about deciphering why specific individuals act the way they do in isolated cases. Rather, it's about identifying a consistent structural pattern—a recognizable architectural signature that emerges repeatedly across different unconnected subjects, suggesting a systematic influence rather than independent personal decisions. Having examined how algorithms function as automated handlers shaping behavior and identity at scale, we must now consider a profoundly troubling question—could these same influence mechanisms potentially manifest in acts of violence? This section requires our most careful examination, deepest respect, and sincere compassion, as it involves immense human suffering and tragedy that has devastated countless families and communities. I approach this topic not to sensationalize but to understand patterns that may help prevent—or at least better understand—future tragedies. The victims and their families deserve nothing less than our most thoughtful analysis of these events.
To be absolutely clear: I'm not conducting investigative journalism on individual cases, nor am I attempting to litigate specific events. Rather, I'm applying the pattern recognition methodology we've used throughout this series—looking for recurring architectural signatures across seemingly unrelated incidents that might reveal deeper systemic connections.
When viewed through this wider aperture, certain consistent elements emerge across mass shooting cases that prompt questions about possible influence mechanisms at work. A hard look at these patterns is essential precisely because of how these events affect public safety and touch the lives of real people and communities who've suffered unimaginable loss.
When analyzed closely, these mass violence incidents show connections that force us to confront unsettling questions about how laboratory techniques, theatrical staging, and networked distribution might converge. Examining these events through our established framework uncovers structural similarities that cannot be easily dismissed as coincidence.
The Architecture of Violence?
Just as we've seen with the OJ Simpson trial—where most Americans became invested in competing narratives that fractured us along predictable lines—mass shootings have (understandably) become a battleground for opposing worldviews. Some advocate for more guns for protection while others demand their removal. Both sides react precisely as predicted, yet neither addresses the disturbing patterns that emerge when viewed through our pattern recognition framework.
Dave McGowan's groundbreaking work Programmed to Kill: The Politics of Serial Murder provides a methodological approach that transcends mainstream explanations. Through meticulous documentation of cases spanning decades, McGowan revealed how seemingly random acts of violence often share architectural signatures suggesting the possibility of systematic coordination rather than coincidence.
McGowan demonstrated how serial killers like Henry Lee Lucas (who claimed over 100 murders) had documented connections to intelligence agencies and exhibited classic signs of programming—including missing time, contradictory statements, and sudden personality shifts identical to those we observed in MKULTRA subjects. His research established that Lucas and others like him weren't merely disturbed individuals but potentially networked nodes in a larger system of controlled violence—a template that applies with disturbing precision to contemporary mass shootings.
McGowan's work connects directly to declassified government programs like The Phoenix Program—the Vietnam War's CIA assassination program that targeted thousands based on algorithmic prediction models. This historical precedent demonstrates the intelligence community's willingness to use systematic violence for control objectives. The Jason Bourne films, drawing heavily from actual CIA programs like Treadstone and MKULTRA, reflect this operational reality in fictional form—not as fantasy but as artistic representation of documented practices.
The Chilling Prediction
In 1991, former Naval Intelligence officer Milton William Cooper wrote in "Behold a Pale Horse" what would prove to be a disturbingly accurate prediction:
"The government encouraged the manufacture and importation of firearms for the criminals to use. This is intended to foster a feeling of insecurity, which would lead the American people to voluntarily disarm themselves by passing laws against firearms... using drugs and hypnosis on mental patients" to create "assassins" who would shoot at schoolyards and "perpetuate other violent acts."
Cooper's pattern recognition extended beyond his written work about school shootings. In this recording from his radio show The Hour of the Time on June 28, 2001—just 75 days before the September 11 attacks—he predicted with unsettling accuracy a coming attack that would be blamed on bin Laden and used to justify removing Americans' freedoms:
The precision of this forecast, made specifically when mainstream discourse gave no indication of such a possibility, demonstrates the effectiveness of pattern recognition when applied to intelligence operations and media narratives. Before Cooper's prediction, school shootings were virtually unheard of. After his writing, they became a regular feature of American life—often involving precisely the psychiatric patients on medication he described. Cooper wasn't making vague prophecies but specific forecasts that manifested with eerie precision.
Cooper would be killed in a police shootout at his home in Eager, Arizona on November 5, 2001, less than two months after the September 11th attacks he predicted—adding another layer to his complex legacy as the original alternative researcher, far more measured and accurate than his modern counterparts.
Systematic Signatures
Applying Schiffer's pattern recognition framework—which emphasizes that "any single fact can be debated... but a pattern that converges across multiple domains is undeniable"—we see structural similarities across events that should have no connection.
These mass shooting events consistently share multiple signatures that create what Schiffer terms "multi-vector coherence":
Psychiatric Medication: Perpetrators often have histories at specific institutions, frequently prescribed SSRIs that can fundamentally alter personality and behavior
Intelligence Connections: Familial ties to military or intelligence agencies
Prior Monitoring: FBI awareness or interaction with the subjects before incidents
Conflicting Narratives: Multiple witness reports contradicting official accounts
Legislative Impact: Incidents consistently generate political support for specific policy changes that would otherwise face stronger opposition
The SSRI connection demands particular attention. Extensive documentation shows that SSRIs can trigger akathisia—a state where patients report feeling 'possessed' or influenced by 'dark forces'—precisely matching the 'hearing voices' pattern we've observed across multiple mass shooters. According to FDA warnings, "any abrupt change in dose whether starting on, increasing or decreasing or discontinuing the drug... can cause suicide, hostility or psychosis." The Physicians' Desk Reference explicitly lists "Manic Reaction," "Abnormal Thinking," and "Hostility" among SSRI side effects.
Laura Delano's memoir about psychiatric medication further documents how these drugs can profoundly alter perception and behavior, creating dramatic personality changes and perceptual shifts. When considered alongside the neural influence technologies documented in our patent section, the potential for exploitation becomes a legitimate concern.
The "Hearing Voices" Pattern
Most disturbingly, a remarkable number of mass shooters report hearing voices commanding them to commit violence—creating another vector of convergence that aligns precisely with the "Voice of God" weapons technology documented in our patent section:
Among numerous documented cases, six high-profile perpetrators—Cruz, Santiago, Alexis, Loughner, May, and Card—described hearing voices directing their violence, from Cruz's "demons" commanding him to "burn, kill, destroy" to Santiago's explicit claims of "government mind control." Is it merely coincidence that these shooters describe experiences that precisely match the capabilities of classified neuroweapons? The pattern suggests otherwise
Historical Precedent: The Hinckley Pattern
Long before modern mass shootings, John Hinckley Jr.’s 1981 attempted assassination of President Reagan revealed the same architectural signatures, showing how these patterns have persisted across decades. Hinckley claimed his actions were motivated by an obsession with actress Jodie Foster and her role in the film Taxi Driver, a film steeped in alienation and vigilante violence—a perfect convergence of The Theater (media programming) and The Network (acting out programmed behavior).
What elevates this case beyond mere obsession are the institutional connections that characterize our pattern recognition framework. The Hinckley family maintained close ties with the Bush family through oil industry networks—John Hinckley Sr. was a substantial political donor and associate of then-Vice President George H.W. Bush, former CIA Director. Most tellingly, Hinckley's brother Scott had scheduled dinner with Bush's son Neil for the very next day after the shooting—a meeting quietly canceled after the assassination attempt. Had Hinckley succeeded, former CIA Director Bush would have ascended to the presidency.
The institutional pattern deepens further through Hinckley's psychiatric confinement. He was sent to St. Elizabeths Hospital, a facility later revealed to have served as a CIA site for involuntary confinement of security risks. The hospital was associated with Dr. Louis Jolyon West—you remember, the same MKULTRA researcher who not only examined Jack Ruby after the Kennedy assassination but also researched truth serums for intelligence agencies and psychiatrically profiled both Oswald and Ruby for the Warren Commission. This creates another striking multi-vector convergence: the same CIA-connected psychiatrist evaluating key figures in both Kennedy's assassination and Reagan's attempted assassination.
These interlocking connections—media programming, intelligence proximity, institutional oversight, and appearance of the same key figures across seemingly unrelated events - create precisely the signature pattern we've documented in contemporary cases. The Hinckley incident demonstrates that the architectural features of potentially programmed violence have remained consistent for decades, only evolving in their technological implementation. With the Hinckley case as a historical benchmark, we now turn to more recent examples that further illuminate The Network’s role in programmed violence.
More Case Studies: The Pattern Made Visible
The 1999 Columbine school massacre—where two students killed 13 people and wounded 24 others at Columbine High School in Colorado—demonstrates this pattern with disturbing clarity. Shooters Eric Harris and Dylan Klebold were prescribed SSRIs documented to increase violent ideation in some subjects. The FDA would later issue black-box warnings about increased suicide risk, but the connection to violence remains under-discussed. According to the FDA's own warnings, added to SSRI antidepressant labels in 2004-2007, “any abrupt change in dose whether starting on, increasing or decreasing or discontinuing the drug... can cause suicide, hostility or psychosis”. The Physicians' Desk Reference explicitly lists 'Manic Reaction,' 'Abnormal Thinking,' 'Hostility,' and 'Paranoid Reactions' among SSRI side effects. Medical research has documented that “over 200,000 people a year enter a general hospital with a diagnosed antidepressant-associated mania and/or psychosis”. The International Coalition for Drug Awareness has documented at least 48 school shootings/incidents involving SSRIs, creating a pattern that cannot be dismissed as coincidence.
Harris's father worked for the military, moving the family repeatedly—while this is common for military families in general, it's also a pattern frequently seen in intelligence-connected families. This connection reflects a broader regional context: Columbine itself grew significantly during the Space Race era due to the Martin Company missile facility (now Lockheed Martin) in nearby Waterton Canyon. While not unique to Columbine specifically, this created a community with connections to aerospace and defense sectors—noting this institutional proximity isn't about questioning the honorable service of military families, who deserve our respect and gratitude. Rather, it identifies another potential data point in the recurring pattern of institutional connections.
An FBI agent's son filmed a school shooting project at Columbine shortly before the attack. Multiple witnesses reported additional shooters never acknowledged officially. Most unsettling: Eric Harris’ alleged writings about crashing planes into NYC skyscrapers—a detailed fantasy that became reality two years later.
The Aurora theater shooter James Holmes received treatment from Dr. Lynne Fenton, a former Air Force psychiatrist with security clearance who previously served as Chief of Physical Medicine for the U.S. Air Force in San Antonio. Holmes allegedly sent her a notebook detailing his plans before the shooting and later stated he believed the FBI would stop him—suggesting either delusion or awareness of potential monitoring.
This pattern of convergence extends to recent high-profile events. The 2024 Trump assassination attempts, while still unfolding and uncertain in many details, reveal elements that align with the architectural signatures we've been tracing—not as anything close to definitive proof but as additional data points in The Network's pattern.
The 2024 Butler, Pennsylvania attempt featured Thomas Crooks, whose parents were both behavioral therapists specializing in rehabilitation—connecting directly to the psychological programming methods we examined in Part 1. Notably, Crooks briefly appeared in a 2022 BlackRock advertisement as a student—a connection the company has since acknowledged while removing the video from circulation.
This pattern recognition approach is gaining traction alongside growing public awareness of MKULTRA's historical reality. Following the 2024 Trump assassination attempt, outlets like BBC immediately labeled any questioning of official narratives as "QAnon conspiracy theories"—employing a deliberate linguistic tactic to associate legitimate inquiry with fringe extremism. The implication is clear: those examining connections between Crooks and institutional influences should be scorned and ridiculed as tin foil hat wearers—a manipulative comparison designed to shut down legitimate inquiry.
What's particularly interesting is the CIA's unprecedented public denial of any MKUltra connection to Thomas Crooks - an extraordinarily unusual step for an agency that typically ignores fringe theories. As Gizmodo reported in July 2024, "The CIA... decided to push back very publicly against these claims, something the agency doesn't often do." This defensive reaction itself becomes another data point in the pattern - when institutional voices feel compelled to actively deny connections rather than simply ignore them, it often signals exactly where attention should be focused.
The 2024 Palm Beach attempt involved Ryan Routh, a Ukraine war zealot whose fixation mirrors exactly the algorithmic cause-shifting we documented in our analysis of NPC programming. Routh published a 291-page book espousing elimination of Trump and advocating for nuclear conflict with Russia—precisely the type of programmed narrative we've seen algorithmically amplified. Footage shows Routh at pro-Ukraine rallies in Kyiv in 2022, demonstrating his deep investment in this cause.
I have no idea what actually happened with either incident, but at what point do statistical anomalies become meaningful patterns? The consistent convergence of multiple elements—from psychiatric backgrounds to algorithmic narrative alignment to institutional connections—creates a signature that’s hard to brush off as mere coincidence under Schiffer's framework.
The FBI Foreknowledge Pattern
A particularly disturbing pattern of FBI foreknowledge emerges across cases. In multiple significant mass shootings of the past decade, the FBI had direct contact with perpetrators before attacks occurred. Nidal Hasan (Fort Hood shooter) was known to the FBI as dangerous, yet this information wasn't forwarded to the Army. The FBI interviewed both Tamerlan Tsarnaev (Boston Marathon bomber) and Omar Mateen (Pulse nightclub shooter) prior to their attacks. Nikolas Cruz (Parkland school shooter) was the subject of specific warnings that went unaddressed.
This pattern doesn't necessarily suggest complicity but raises questions about systemic failures. The consistency across unrelated cases—where the same agency identifies potential threats yet fails to prevent violence—creates another convergence point that reveals another signature pattern that fits within our analytical framework.
Media Lifecycle Predictability
Each incident follows an identical media progression: initial shock and confusion, competing narratives from witnesses, rapid consolidation around an official story, and immediate leveraging for pre-existing policy agendas. This consistency transforms seemingly random tragedy into functional components within a larger control architecture.
Just as the OJ trial created two Americas with irreconcilable viewpoints, mass shootings create predictable social division—conservative calls for more security versus progressive demands for gun control. Both sides respond exactly as forecast, creating precisely the kind of engineered schismogenesis we've documented throughout this series.
The Human Cost
Having a deep personal connection to families affected by one of these shootings, I can attest to the deep-seated and lasting devastation these events cause. The trauma extends far beyond the immediate victims to shatter entire communities. Families are torn apart, neighborhoods transformed, and children's sense of safety permanently altered. The media cycle moves on, but the communities never fully recover.
This reality demands that we approach this topic with the utmost sensitivity. The pain is genuine and deep, regardless of what patterns may lie beneath. Our exploration seeks not to exploit this suffering but to honor victims by pursuing deeper understanding.
The Network Convergence
These mass violence incidents represent a convergence of everything we've examined:
The Laboratory techniques of programming developed in MKULTRA
The Theater's performers and scripts that captivate public attention
The technological delivery systems of The Network
The algorithmic attention direction we observed with the NPC phenomenon
Whether intentional or not, these incidents create the same effects that emerge in the MKULTRA documentation: social division, surveillance expansion, and control through fear.
I share these patterns not to make definitive claims but to illuminate connections that deserve our consideration. When viewed through pattern recognition methodology, these events display architectural signatures that cannot be dismissed as coincidence. The consistency across cases, despite their apparent independence, creates what Schiffer calls "a pattern that converges across multiple domains"—the signature of design rather than chance.
As we've traced the evolution from laboratory experiments to theatrical performances to networked distribution, mass shootings represent the most disturbing convergence of these systems.
From these darkest expressions of potential programming, we turn next to where our journey began: the mass amnesia experienced at Taylor Swift's concerts. Though vastly different in context and consequence, both phenomena may represent different applications of the same fundamental technologies—techniques for altering consciousness at scale through engineered environments optimized for neural influence. What connects a potential mass shooter's programming to concert amnesia isn't content but pattern—the same architectural signature of consciousness manipulation operating through different delivery systems.
•••
Taylor Swift Concert Amnesia: The Network at Scale
Our exploration of mind control's evolution began with Taylor Swift fans experiencing inexplicable memory loss—a contemporary phenomenon that opened our investigation into techniques stretching back decades. Having traced these methods from laboratory experiments to theatrical performances to technological systems, we now return to this opening mystery, understanding it as The Network operating at mass scale.
"It's almost like my brain couldn't process what was happening... I don't remember a single thing." - Taylor Swift concert attendee, as reported by ABC News
As reported by ABC News and other mainstream outlets, numerous attendees of Swift's Eras Tour described experiencing partial or complete memory loss despite being fully conscious during performances. "It's almost like my brain couldn't process what was happening," one fan described. Another reported: "I don't remember a single thing."
What are the chances that thousands of unrelated people across different venues would all experience the exact same memory pattern? That they'd remember arriving and leaving but draw a blank on the actual performance? This selective amnesia echoes the compartmentalized memory techniques developed in MKULTRA—now seemingly operating at stadium scale without any chemicals or electrodes required.
From Dissociation to Digital Amnesia
While mainstream explanations attribute this to normal sensory overload, the parallels to documented mind control effects are unmistakable:
Dissociation Induction: Pulsing lights and specific sound frequencies create the same dissociative states induced in MKULTRA laboratories
Memory Compartmentalization: The selective forgetting mirrors compartmentalized amnesia—core objective of early programming experiments
Post-Hypnotic Effects: Attendees remember entering and leaving but not the performance itself, matching hypnotic amnesia patterns
Mass Synchronization: Thousands experiencing identical memory gaps suggests neural conditioning mechanisms affecting brain function collectively
Technical Analysis of the Concert Environment
The concert setting provides ideal conditions for applying technologies documented in our previous sections:
Precisely calibrated sound frequencies capable of cognitive capture
Synchronized lighting patterns matching documented brainwave manipulation techniques
Emotional elevation creating heightened suggestibility states
Voluntary participation with subjects who are expecting and are primed for emotional impact
Neuroscientist Michael Persinger documented how specific electromagnetic frequencies can induce altered states of consciousness through temporal lobe stimulation—including sensed presences, unusual perceptions, and modifications to subjective time perception. Similar principles of electromagnetic influence on consciousness could potentially be employed through sophisticated concert production systems
Historical Context: Beyond Beatlemania
This isn't the first mass effect observed at performances. Beatles concerts produced "mass hysteria" with synchronized emotional states, while political rallies throughout history have demonstrated similar patterns of collective emotional response. Hitler's Nuremberg rallies, for instance, were meticulously choreographed with architecture, lighting, and sound designed to create a specific psychological impact. What's undeniable is that the technical capability to influence group emotional states through sensory stimuli existed long before digital technology—making these collective responses worth examining through our pattern recognition framework.
It's important to emphasize that while the technical capability for inducing mass amnesia does exist, and the pattern matches documented mind control effects, there is no definitive evidence that Taylor Swift concerts deliberately involve memory manipulation. The typical explanation—that sensory overload and emotional intensity create natural dissociative states—remains plausible.
However, when viewed through our pattern recognition framework, several anomalies emerge that conventional explanations struggle to address: the selective nature of the memory loss (remembering being at the concert but not specific performances), the scale of effect across thousands of attendees simultaneously, and the consistency of the phenomenon across different venues and performances.
What's most remarkable isn't that it's happening, but that we've normalized it. Parents worldwide aren't alarmed when their teenagers return home with fractured memories—they attribute it to excitement, exhaustion, or being "star-struck." Yet what we're observing mirrors precisely what MKULTRA researchers documented in their studies of dissociative states.
The Network Completes Its Evolution
The Swift concert amnesia represents The Network's evolution to its logical conclusion: influence technologies seamlessly integrated into cultural experiences. No coercion necessary when millions eagerly purchase tickets to experiences that alter their consciousness in carefully engineered environments.
While our primary focus remains on the documented memory anomalies experienced by concert attendees, it's worth noting that Swift's cultural influence extends beyond neurological effects. Former State Department official and digital sovereignty advocate Mike Benz has detailed her role within broader influence ecosystems—highlighting how her music catalog was acquired by investment groups linked to defense and intelligence sectors, including the Carlyle Group. Swift has been strategically deployed in political campaigns and even featured in NATO Psychological Operations Center presentations as a case study in mass influence.
These connections gain further weight in light of her lineage. Her great-grandfather, Archie Dean Swift, served as head of the Federal Reserve Bank of Philadelphia—establishing a multi-generational tie to institutional power structures. Whether these associations represent intentional alignment or merely reflect her value as a high-leverage cultural asset, they reinforce the pattern of entertainment figures serving as conduits for broader control systems.
The Federal Reserve itself acknowledged Swift's influence in 2023, crediting her Eras Tour with boosting hotel revenues across the country—a literal demonstration of how engineered cultural phenomena can move markets and recondition behavior at national scale. While the amnesia effect remains our focus—mirroring the dissociative states MKULTRA researchers once induced through chemicals and trauma—the context surrounding Swift underscores just how far the system has evolved. Today, neurological entrainment, economic mobilization, and perception shaping can all occur through a single engineered event presented as entertainment.
The isolated dissociation once induced with LSD and electroshock now manifests through precisely engineered sound, light, and emotional triggers—reaching thousands simultaneously without a single drop of acid.
For the millions of parents who've watched their teens return from these shows with fragmented memories, what you're witnessing isn't just fandom. It's the culmination of decades of research into consciousness manipulation, now deployed through entertainment that your children saved their allowance to experience.
The Grateful Dead's acid tests required chemical compounds and personal attendance. Today's mass influence operates through technologies that can replicate similar effects without chemical assistance—and potentially reach billions through livestreams and social media. The Theater has expanded beyond physical venues to encompass digital participation, with the same technological principles operating regardless of where you watch.
From programming individual assassins to orchestrating mass amnesia, The Network scales from one to billions. The techniques originally developed in underground laboratories now hide in spotlights, concealed behind spectacle while achieving the same cognitive effects on industrial scale.
This isn't speculative futurism—it's actively under development for consumer release. Meta’s Zuckerberg confirmed that neural interface glasses capable of displaying holograms and responding to mental commands will likely be available "hopefully closer to four [years]" from now. The same capabilities once requiring classified facilities are being openly developed as consumer products.
You're not just watching the show. You've become part of it. The Network has completed its evolution from external imposition to willing participation—the ultimate achievement of any system of control. This evolution connects all the pieces we've examined—from laboratory experiments to theatrical performances to our individual digital devices. The pattern recognition framework reveals not isolated phenomena but a cohesive system that has transformed how control operates in our society.
Recognition is the first step toward liberation. As we continue to explore these patterns, we begin to see not just how the systems shape us, but how we might reclaim our cognitive sovereignty in a world that increasingly treats consciousness as just another programmable space.
From Mass Amnesia to Individual Awakening
The evolution from isolated test subjects in secret facilities has expanded to fill stadiums.The isolated dissociation once induced with LSD and electroshock now manifests through precisely engineered sound, light, and emotional triggers—reaching thousands simultaneously without a single drop of acid. The question becomes not just how this happened, but what it means for our understanding of our own minds.
•••
Conclusion: The Network as Living Entity
Mind control has evolved from MKULTRA's crude laboratory experiments to a sophisticated ecosystem capable of influencing billions simultaneously—from mass trauma events and institutional programming to the device in your pocket. The Network operates as a living entity whose reach extends through blue light frequencies, electromagnetic fields, and algorithmic systems—not merely causing addiction but actively shaping perception and behavior through the same fundamental principles once tested in classified settings. This isn't about technology dependence—it's about the deliberate application of consciousness manipulation techniques at unprecedented scale.
Neil Postman's warning in Amusing Ourselves to Death predicted this shift: control would arrive not as Orwell's boot but as Huxley's pleasure. The Network delivers precisely this transformation of coercive programming into voluntary participation. The technological lineage is documented:
From trauma-based MKULTRA programming to patents for nervous system manipulation via consumer screens
From handler-subject relationships to algorithmic systems that monitor and direct behavior
From experimental compounds to Voice of God technologies and electromagnetic fields that influence neural activity
From individual programming to mass amnesia at Swift concerts, programmed violence in mass shooters, and ritual programming through Olympic ceremonies
If these connections feel overwhelming, that's by design. The Network doesn't just create addiction—it induces specific cognitive states that mirror the dissociation, suggestibility, and compartmentalization documented in classified mind control programs. The paradox is that you're likely reading this analysis on the very devices that function as delivery mechanisms for these influence technologies.
Next time your phone buzzes, recognize beyond the addiction pattern:
The trigger-response conditioning mirroring MKULTRA techniques
The induced state of heightened suggestibility following the notification
The directed focus shaped by algorithmic curation
The loss of time awareness characteristic of hypnotic states
This isn't habit formation—it's The Network's tendrils engaging with your neurology through techniques pioneered in classified settings. What MKULTRA once achieved through trauma and drugs, The Network now replicates through digital immersion and frequency—only now, the subjects finance their own programming
As we'll explore in Part 4, the fight for cognitive sovereignty requires understanding that technology addiction is merely the delivery mechanism for more transformative consciousness manipulation. You thought the show was outside, but The Network's influence has woven itself directly into neural pathways. The Laboratory created the methods, The Theater staged the performances, The Network deployed them to billions—and now we face The Mirror, where we confront not just habits but the systematic programming of perception itself.
•••
Works Cited (Part 3: In Order of Mention)
Stylman, Joshua. “MKULTRA: The Hidden Hand, Part 1 - The Laboratory.” Substack, 2025, https://stylman.substack.com/p/mkultra-the-hidden-hand-part-1-the.
Stylman, Joshua. “MKULTRA: The Hidden Hand, Part 2 - The Theater.” Substack, 2025, https://stylman.substack.com/p/mkultra-the-hidden-hand-part-2-the.
United States. Patent Office. Patent US20230225659A1: Monitoring Brain Waves Through AirPods. 2023, https://patents.google.com/patent/US20230225659A1/en.
United States. Patent Office. Patent US6506148B2: Nervous System Manipulation by Electromagnetic Fields from Monitors. 2003, https://patents.google.com/patent/US6506148B2/en.
Central Intelligence Agency. MKULTRA Subproject 136. https://www.cia.gov/readingroom/docs/MKULTRA%20%20SUBPROJECT%20136%20%20%5B8144493%5D.pdf.
“Eunice Simpson, Mother of O.J. and Inspirational Figure, Dies.” SFGate, 2001, https://www.sfgate.com/news/article/Eunice-Simpson-mother-of-O-J-and-inspirational-2858365.php.
Leonard, Tom. “O.J. Simpson’s Father Was a Drag Queen.” Daily Mail, 2024, https://www.dailymail.co.uk/news/article-13299305/OJ-Simpson-dead-dad-drag-queen-TOM-LEONARD.html.
“Carl Colby, Neighbor of Nicole Brown Simpson, Testifies.” Alamy, 1995, https://www.alamy.com/carl-colby-a-neighbor-of-nicole-brown-simpson-testifies-in-los-angeles-feb-3-1995-about-seeing-oj-simpson-outside-nicoles-home-in-1992-colby-said-he-called-911-thinking-the-man-who-he-later-realized-was-simpson-was-a-possible-burglar-ap-photopoolmark-j-terrill-image511001286.html.
BBC. “Was Modern Art a Weapon of the CIA?” BBC Culture, 4 Oct. 2016, https://www.bbc.com/culture/article/20161004-was-modern-art-a-weapon-of-the-cia.
ThePunisherDove, Elizabeth. “The OJ Simpson Connection: Why Didn’t We Hear About Some of This?” Substack, 2024, https://elizabeththepunisherdove.substack.com/i/80094063/the-oj-simpson-connection-why-didnt-we-hear-about-some-of-this.
United States. Advisory Committee on Human Radiation Experiments. “Final Report.” PubMed, 1996, https://pubmed.ncbi.nlm.nih.gov/8683820/.
Stylman, Joshua. “Space, Symbols, and Suspicion.” Substack, 2025, https://stylman.substack.com/p/space-symbols-and-suspicion.
Dyer, Jay. “Analysis of Super Bowl Halftime Show Symbolism.” X, 2024, https://x.com/Jay_D007/status/1821241296977264945.
“Astroworld Festival Crowd Crush.” Wikipedia, 2021, https://en.wikipedia.org/wiki/Astroworld_Festival_crowd_crush.
Harari, Yuval Noah. “Humans Are Now Hackable Animals.” YouTube, 2020,
Schwab, Klaus. “Penetration of Cabinets.” YouTube, 2022,
Stylman, Joshua. X, 2022, https://x.com/jstylman/status/1552666310747750402.
World Economic Forum. “Mind Control Using Sound Waves? We Ask a Scientist How It Works.” Human Synthesis, 2019, https://human-synthesis.ghost.io/2019/06/20/remote-mind-control-using-sound-waves-or-g5/.
World Economic Forum. “Ready for Brain Transparency? Davos AM23.” WEF Videos, 2023, https://www.weforum.org/videos/davos-am23-ready-for-brain-transparency-english/.
World Economic Forum. “Mind and the Machine Panel.” YouTube, 2024,
World Economic Forum. “China Is Monitoring Employees’ Brain Waves.” WEF Stories, 2018, https://www.weforum.org/stories/2018/05/china-is-monitoring-employees-brain-waves-and-emotions-and-the-technology-boosted-one-companys-profits-by-315-million/.
World Economic Forum. “Mind-Controlled Therapeutics by Martin Fussenegger.” YouTube, 2016,
World Economic Forum. “Brain-Computer Interfaces in Healthcare.” WEF Stories, 2025, https://www.weforum.org/stories/2025/01/brain-computer-interfaces-healthcare/.
World Economic Forum. “Virtual Global Collaboration Village.” WEF Press, 2022, https://www.weforum.org/press/2022/05/world-economic-forum-unveils-virtual-global-collaboration-village-as-the-future-of-strong-public-private-cooperation.
Central Intelligence Agency. ARTICHOKE Memo: Can We Get Control of an Individual to the Point Where He Will Do Our Bidding Against His Will?. 1952, https://nsarchive2.gwu.edu/NSAEBB/NSAEBB54/st02.pdf.
United States. Department of Defense. DARPA Programs. https://www.darpa.mil.
United States. Patent Office. Patent US6011991A: Brain Wave Analysis. 2000, https://patents.google.com/patent/US6011991A/en.
United States. Patent Office. Patent US3951134A: Apparatus and Method for Remotely Monitoring and Altering Brain Waves. 1974, https://patents.google.com/patent/US3951134A/en.
United States. Patent Office. Patent US2016/0375220A1: Magnetic Brain Modulation. 2016, https://patents.google.com/patent/US20160375220A1/en.
United States. Patent Office. Patent US20140198035A1: Wearable Muscle Interface Systems, Devices and Methods. 2019, https://patents.google.com/patent/US20140198035A1/en.
United States. Patent Office. Patent US20150045007A1: Mind-Controlled Virtual Assistant on a Smartphone Device. 2014, https://patents.google.com/patent/US20150045007A1/en.
Stylman, Joshua. “Node Without Consent: The Battle Against 6G and the Internet of Bodies.” Substack, 2025, https://stylman.substack.com/p/node-without-consent.
IEEE Standards Association. IEEE 802.15.6: Wireless Body Area Networks. https://standards.ieee.org.
RedPill Drifter. “Mind Influence Technologies Documentation.” X, 2024, https://x.com/RedpillDrifter/status/1799700126757437726.
Stylman, Joshua. “The Technocratic Blueprint.” Substack, 2025, https://stylman.substack.com/p/the-technocratic-blueprint.
“What’s an LRAD? Explaining the Sonic Weapons Police Use for Crowd Control and Communication.” The Conversation, 2021, https://theconversation.com/whats-an-lrad-explaining-the-sonic-weapons-police-use-for-crowd-control-and-communication-177442.
Norris, Woody. “Directional Audio Systems.” Wired, 2004, https://www.wired.com/2004/03/now-hear-this-beat-it/.
Norris, Woody. “TED Talk on Directional Audio Technology.” YouTube, 2004,
United States. Patent Office. Patent US5159703A: Silent Subliminal Presentation System. 1992, https://patents.google.com/patent/US5159703A/en.
United States. Patent Office. Patent US4686605A: High-Frequency Active Auroral Research Program (HAARP). 1987, https://patents.google.com/patent/US4686605A/en.
European Parliament. Report on the Environment, Security and Foreign Policy. Document A4-0005/99, 1999, https://www.europarl.europa.eu/doceo/document/A-4-1999-0005_EN.html.
Kruse, Jack. JackKruse.com. https://jackkruse.com.
MAGACOVFEFE. “MK Ultra Trauma Programming Chart.” X, 9 July 2024, https://x.com/MAGACOVFEFE1711/status/1810665721871073568.
f.lux, https://justgetflux.com.
Iris Tech, https://iristech.co/iris.
DARPA. “Neural Engineering System Design (NESD).” Defense Advanced Research Projects Agency, https://www.darpa.mil/research/programs/neural-engineering-system-design.
DARPA. “Systems-Based Neurotechnology for Emerging Therapies (SUBNETS).” Defense Advanced Research Projects Agency, https://www.darpa.mil/research/programs/systems-based-neurotechnology-for-emerging-therapies.
Wikipedia. “Advanced Aerospace Threat Identification Program.” Wikipedia, https://en.wikipedia.org/wiki/Advanced_Aerospace_Threat_Identification_Program.
Greenson, Ralph. Marilyn Monroe. Doubleday, 1991, https://www.google.com/books/edition/Marilyn_Monroe/r2W9SGUyRmgC?hl=en&gbpv=0.
Haugen, Frances. Facebook Whistleblower Frances Haugen Testifies Before UK Parliament. Rev, 2021, https://www.rev.com/transcripts/facebook-whistleblower-frances-haugen-testifies-before-uk-parliament-transcript.
Kendall, Tim. “Former Facebook Employee: We Made It Addictive Like Cigarettes.” Futurism, 2020, https://futurism.com/the-byte/former-facebook-employee-addictive-cigarettes.
Zuboff, Shoshana. “The Discovery of Behavioral Surplus.” Simon Fraser University, 2018, https://www.sfu.ca/~palys/Zuboff-2018-Ch03-TheDiscoveryOfBehavioralSurplus.pdf.
“Transgender Identification Rates by Birth Year.” X, 2024, https://x.com/gXrubicon/status/1914208873948340718.
Centers for Disease Control and Prevention. “Sexual Orientation and Gender Identity Among U.S. Adults Aged 18–64, by Age Group and Birth Cohort.” MMWR, 2024, https://www.cdc.gov/mmwr/volumes/73/su/su7304a6.htm.
Tavistock Institute. “A Contentious Place: The Inside Story of Tavistock’s NHS Gender Identity Clinic.” The Guardian, 19 Jan. 2023, https://www.theguardian.com/society/2023/jan/19/a-contentious-place-the-inside-story-of-tavistocks-nhs-gender-identity-clinic.
Stylman, Joshua. “The Couch Revolution.” Substack, 2025, https://stylman.substack.com/p/the-couch-revolution.
“NPC Meme Definition.” Later, https://later.com/social-media-glossary/npc/#:~:text=%22NPC%22%20stands%20for%20%22Non,thought%20or%20blindly%20following%20trends.
Sharav, Vera. “Never Again Is Now Global.” Substack, 2025,
McGowan, Dave. Programmed to Kill: The Politics of Serial Murder. iUniverse, 2004, https://www.google.com/books/edition/Programmed_to_Kill/J98kPwAACAAJ?hl=en.
“Phoenix Program.” Wikipedia, https://en.wikipedia.org/wiki/Phoenix_Program.
“Bourne Franchise.” Wikipedia, https://en.wikipedia.org/wiki/Bourne_(franchise).
Pieper, Ryan. “From MK-Ultra to Modern Intelligence: Is a Real-Life Treadstone Program Possible?” Medium, 6 Jan. 2021, https://medium.com/@pieperbrothers0090/from-mk-ultra-to-modern-intelligence-is-a-real-life-treadstone-program-possible-d5c25ea2f934.
Cooper, Milton William. Behold a Pale Horse. Light Technology Publishing, 1991, https://www.google.com/books/edition/Behold_a_Pale_Horse/g0aen3LDErAC?hl=en&gbpv=1&dq=Behold+a+Pale+Horse+pdf&printsec=frontcover.
Schiffer, Mark. “The Pattern Recognition Era: A Manifesto.” Substack, 2025, https://stylman.substack.com/p/the-pattern-recognition-era-a-manifesto.
Vigilant Fox. “Exposed: The Chilling SSRI Link to Mass Shootings.” Vigilant Fox,
International Coalition for Drug Awareness. “SSRI Stories: Antidepressant Nightmares.” SSRIstories, https://ssristories.net.
Preda, Adrian, et al. “Antidepressant-Associated Mania and Psychosis Resulting in Psychiatric Admissions.” The Journal of Clinical Psychiatry, vol. 62, no. 1, 2001, https://www.psychiatrist.com/jcp/antidepressant-associated-mania-psychosis-resulting.
Delano, Laura. Unshrunk. Penguin Random House, 2024, https://www.penguinrandomhouse.com/books/624778/unshrunk-by-laura-delano/.
“Parkland Shooting Suspect Heard Demons.” Washington Post, 2018, https://www.washingtonpost.com/news/post-nation/wp/2018/08/06/parkland-shooting-suspect-told-police-he-heard-a-demon-telling-him-burn-kill-destroy/.
“Santiago Claims Government Mind Control.” AP News, 2017, https://apnews.com/general-news-a1b7f1418f6647d7b10aa908348039dd.
“Navy Yard Shooter Aaron Alexis Heard Voices.” ABC News, 2013, https://abcnews.go.com/US/navy-yard-shooter-aaron-alexis-heard-voices-experienced/story.
“Loughner Pleads Guilty in Arizona Shooting.” CNN, 2012, https://www.cnn.com/2012/08/07/us/arizona-loughner-plea/index.html.
“2014 Florida State University Shooting.” Wikipedia, 2014, https://en.wikipedia.org/wiki/2014_Florida_State_University_shooting.
“Maine Gunman Feared for His Mental State.” ABC News, 2023, https://abcnews.go.com/US/fellow-reservist-feared-maine-gunman-guns-snap/story.
“Ronald Reagan Assassination Attempt.” History.com, https://www.history.com/articles/ronald-reagan-attempted-assassination-john-hinckley-jodie-foster.
“Hinckley’s Life and Connections.” New York Times, 1981, https://www.nytimes.com/1981/04/01/us/a-life-that-started-out-with-much-promise-took-reclusive-and-hostile-path.html.
Kaye, J. “CIA-Connected DC Hospital Chief Advised on Hinckley.” Substack,
“Louis Jolyon West.” Wikipedia, https://en.wikipedia.org/wiki/Louis_Jolyon_West.
“Eric Harris’s Parents.” Very Celeb, https://veryceleb.com/who-are-eric-harris-parents/.
“Columbine, Colorado.” Wikipedia, https://en.wikipedia.org/wiki/Columbine%2C_Colorado.
“Columbine Shooting Reports.” Denver Post, 2000, https://extras.denverpost.com/news/shot0513b.htm.
“Columbine Mafia Writings.” Denver Post, 2000, https://extras.denverpost.com/news/colreport/Columbinerep/Pages/MAFIA_TEXT.htm.
“Columbine Bibliography.” Crime Library, https://crimelibrary.org/notorious_murders/mass/littleton/bibli_8.html.
“2012 Aurora Theater Shooting.” Wikipedia, https://en.wikipedia.org/wiki/2012_Aurora_theater_shooting.
“Dr. Lynne Fenton’s Bio.” Economic Policy Journal, 2012, https://www.economicpolicyjournal.com/2012/07/dr-lynne-fentons-bio-that-was-deleted.html.
“James Holmes’s Diary.” Time, 2015, https://time.com/3899063/james-holmes-diary-aurora-theate-shooting/.
“Holmes Wished Psychiatrist Had Locked Him Up.” CBS News, 2015, https://www.cbsnews.com/news/colorado-theater-gunman-james-holmes-says-he-wishes-psychiatrist-had-locked-him-up/.
“FBI Statement on Butler, Pennsylvania Incident.” FBI.gov, 2024, https://www.fbi.gov/news/press-releases/fbi-statement-on-incident-in-butler-pennsylvania.
“CIA Denies MKULTRA Connection to Thomas Crooks.” Wired, 2024, https://www.wired.com/story/thomas-crooks-conspiracy-donald-trump-cia-mk-ultra/.
“CIA Denies Conspiracy Theory on Trump Shooter.” Gizmodo, 2024, https://gizmodo.com/cia-denies-conspiracy-theory-that-it-used-mkultra-on-trump-shooter-2000479562.
“BBC on Trump Assassination Attempt Conspiracies.” BBC, 2024, https://www.bbc.com/news/articles/cyr7pyd0687o.
“Ryan Routh’s Book and Ukraine Advocacy.” Times of Israel, 2024, https://www.timesofisrael.com/would-be-trump-assassin-urged-iran-to-kill-ex-president-in-his-book-about-ukraine/.
“Nidal Hasan Missed by FBI.” CBS News, 2011, https://www.cbsnews.com/news/nidal-malik-hasan-update-fbi-missed-ticking-time-bomb-says-ft-hood-report.
“FBI Knew of Boston Bombing Suspect.” Politico, 2013, https://www.politico.com/blogs/under-the-radar/2013/06/fbi-knew-earlier-of-boston-bombing-suspect-166313?.
“FBI Statement on Parkland Shooting.” FBI.gov, 2018, https://www.fbi.gov/news/press-releases/fbi-statement-on-the-shooting-in-parkland-florida.
“Taylor Swift Fans Who Experienced ‘Post-Concert Amnesia’ Are Not Alone: ‘I Don’t Remember a Single Thing’.” ABC News, 26 Oct. 2023, https://abcnews.go.com/GMA/Wellness/taylor-swift-fans-experienced-post-concert-amnesia-luck/story?id=103839859.
Persinger, Michael A., and Stanley A. Koren. “Experimental Facilitation of the Sensed Presence: Possible Intercalation Between the Hemispheres Induced by Complex Magnetic Fields.” The Journal of Nervous and Mental Disease, vol. 190, no. 8, 2002, pp. 533–541. https://pubmed.ncbi.nlm.nih.gov/12193838/.
Benz, Mike. “Taylor Swift’s Role in Influence Ecosystems.” X, 2024, https://x.com/MikeBenzCyber/status/1744633598408319432.
Federal Reserve Bank of Philadelphia. “Archie Dean Swift.” Bank Lookup, https://banklookup.spmc.org/banker/69405?bank=723.
Federal Reserve Board. “Taylor Swift’s Eras Tour Boosts Hotel Revenues.” NBC News, 2023, https://www.nbcnews.com/business/consumer/taylor-swift-federal-reserve-credits-eras-tour-boosting-hotels-tourism-rcna94046.
Zuckerberg, Mark. “Neural Interface Glasses Development.” YouTube, 2025,
Postman, Neil. Amusing Ourselves to Death: Public Discourse in the Age of Show Business. Penguin Books, 1985, https://archive.org/details/amusingourselves0000post.
•••
Appendix A: Partial Neural Interface Patent List
Consciousness Bypass Technologies
SUBLIMINAL VISUAL SYSTEMS
US4717343 (1988) - "Method of Changing a Person's Behavior"
Conditions unconscious mind through visual programming without therapist
Claims to replace "undesirable mental images" with "desirable" ones https://patents.google.com/patent/US4717343
US4616261 (1986) - "Method of Generating Subliminal Visual Messages"
Superimposes subliminal messages over standard television broadcasts
Uses computer to generate and time message display with video synchronization https://patents.google.com/patent/US4616261
US4692118 (1987) - "Video Subconscious Display Attachment"
Device that attaches to video displays to insert subliminal content
Enables covert insertion of messages into standard video content https://patents.google.com/patent/US4692118
US5551879 (1996) - "Dream State Teaching Machine"
Targets subconscious during sleep or altered states of consciousness
Uses visual stimuli to imprint information during dream states https://patents.google.com/patent/US5551879
SUBLIMINAL AUDIO SYSTEMS
US5159703A (1992) - "Silent Subliminal Presentation System"
Uses inaudible high-frequency carriers to transmit subliminal messages
Modulates messages into ultrasonic range undetectable by conscious mind https://patents.google.com/patent/US5159703A
US4777529A (1988) - "Auditory Subliminal Programming System"
Encodes subliminal messages with security tones for authorized playback
Combines subliminal content with low-frequency signals for "relaxation" https://patents.google.com/patent/US4777529A
US4395600A (1983) - "Auditory Subliminal Message System and Method"
Adjusts subliminal message amplitude based on ambient audio signals
Designed for retail environments to deter shoplifting through suggestion https://patents.google.com/patent/US4395600A
US4924744 (1990) - "Apparatus for Generating Sound through Low Frequency & Noise Modulation"
Creates subliminal messages through low-frequency modulation techniques
Uses noise to mask and deliver content below conscious perception https://patents.google.com/patent/US4924744
US5170381 (1992) - "Method for Mixing Audio Subliminal Recordings"
Combines multiple subliminal audio tracks for enhanced effectiveness
Creates layered subliminal content for deeper psychological impact https://patents.google.com/patent/US5170381
DE3628420A1 (1986) - "Device for reproducing voice information in a subliminal technique"
German patent for subliminal voice information delivery
Enables covert reproduction of voice messages below conscious awareness https://patents.google.com/patent/DE3628420A1
US60552336 - "Apparatus & Method of Broadcasting Audible Sound Using Ultrasonic Sound as a Carrier"
Delivers audible content through ultrasonic carrier waves
Creates directional audio that can target specific individuals https://patents.google.com/patent/US60552336
BRAIN ENTRAINMENT
US5954630 (1999) - "FM Theta-Inducing Audible Sound, & Method, Device & Recorded Medium"
Uses specific sound frequencies to induce theta brainwave states
Alters consciousness through FM audio manipulation techniques https://patents.google.com/patent/US5954630
US5954629 (1999) - "Brain Wave Inducing System"
Generates specific brainwave patterns through external stimulation
Synchronizes neural activity to predetermined frequencies https://patents.google.com/patent/US5954629
US5330414 (1994) - "Brain Wave Inducing Apparatus"
Device designed to alter brainwave patterns through targeted stimulation
Creates specific mental states through frequency entrainment https://patents.google.com/patent/US5330414
US5213562 (1993) - "Method of Inducing Mental, Emotional & Physical States of Consciousness"
Induces specific mental states through precisely designed audio patterns
Claims to alter consciousness at will through audio entrainment https://patents.google.com/patent/US5213562
US5151080 (1992) - "Method & Apparatus for Inducing & Establishing a Changed State of Consciousness"
Creates altered consciousness states through specific stimulation patterns
Enables establishment of predefined mental states through external means https://patents.google.com/patent/US5151080
US5135468 (1992) - "Method & Apparatus of Varying the Brain State of a Person by Means of an Audio Signal"
Manipulates brain states through specialized audio signals
Targets specific neural frequencies to create desired mental conditions https://patents.google.com/patent/US5135468
US5586967 (1996) - "Method & Recording for Producing Sounds & Messages To Achieve Alpha & Theta Brainwave States"
Creates audio recordings to induce specific brainwave patterns
Designed to place listeners in receptive alpha and theta states https://patents.google.com/patent/US5586967
US7674244 (2010) - "Method for Incorporating Brain Wave Entrainment into Sound Production"
Embeds brainwave-altering frequencies into standard audio content
Enables covert neural influence through everyday sound environments https://patents.google.com/patent/US7674244
US5289438 (1994) - "Method and System of Altering Consciousness"
System designed to alter conscious awareness states
Applies rhythmic stimulation techniques to modify neural activity https://patents.google.com/patent/US5289438
US8579793 (2013) - "Apparatus To Effect Brainwave Entrainment over Premises Power-Line Wiring"
Delivers brainwave entrainment signals through building power lines
Affects everyone in a building through electromagnetic fields from wiring https://patents.google.com/patent/US8579793
US20140309484A1 (2014) - "Method & System for Brain Entrainment"
Advanced technique for synchronizing brain activity to external stimuli
Creates targeted neural states through precision entrainment methods https://patents.google.com/patent/US20140309484A1
US8636640 (2014) - "Method & System for Brain Entertainment"
System for inducing pleasurable brain states through external stimulation
Creates entertainment experiences through direct neural manipulation https://patents.google.com/patent/US8636640
US4834701 (1989) - "Apparatus for Inducing Frequency Reduction in Brain Wave"
Reduces brain wave frequency through external stimulation
Creates altered states by slowing neural oscillation patterns https://patents.google.com/patent/US4834701
Direct Neural Manipulation Systems
ELECTROMAGNETIC FIELD TECHNOLOGIES
US6506148B2 (2003) - "Nervous System Manipulation by EM Fields from Monitors"
Manipulates nervous system via electromagnetic fields from screens
Pulses images at specific frequencies (0.5Hz or 2.4Hz) to affect viewers https://patents.google.com/patent/US6506148B2
US2016/0375220A1 (2016) - "Magnetic Fields for Modulating Brain Activity"
Uses magnetic fields to alter brain function in targeted ways
Allows external control of neural processes through magnetic stimulation https://patents.google.com/patent/US2016/0375220A1
US6238333B1 (2001) - "Remote Magnetic Manipulation of Nervous Systems"
Uses rotating magnetic fields to affect the nervous system from a distance
Creates physiological effects through weak magnetic fields at specific frequencies https://patents.google.com/patent/US6238333B1
US5935054A (1999) - "Magnetic Excitation of Sensory Resonances"
Stimulates the nervous system with weak magnetic fields near 1/2 Hz
Can induce relaxation, drowsiness, or other physiological effects https://patents.google.com/patent/US5935054A
US5782874 (1998) - "Method & Apparatus for Manipulating Nervous Systems"
System for directly influencing nervous system function through external means
Creates targeted neurological effects through precision stimulation https://patents.google.com/patent/US5782874
US5899922 (1999) - "Manipulation of Nervous Systems by Electronic Fields"
Uses electronic fields to alter nervous system function remotely
Creates physiological and psychological effects through field exposure https://patents.google.com/patent/US5899922
US6167304 (2000) - "Pulse Variability in Electric Field Manipulation of Nervous System"
Uses variable pulse patterns in electric fields to affect neural function
Creates unpredictable stimulation to prevent nervous system adaptation https://patents.google.com/patent/US6167304
US6081744 (2000) - "Electric Fringe Generator for Manipulating Nervous Systems"
Creates electric field fringes to manipulate the human nervous system
Enables targeted influence on neural activity through field effects https://patents.google.com/patent/US6081744
US6091994 (2000) - "Pulsative Manipulation of Nervous Systems"
Uses pulsed signals to create targeted effects on nervous system function
Enables rhythmic disruption or enhancement of neural processes https://patents.google.com/patent/US6091994
US3393279 (1968) - "Nervous System Excitation Device"
Early technology for direct stimulation of the nervous system
Creates excitation in neural tissue through external means https://patents.google.com/patent/US3393279
US6017302 (2000) - "Subliminal Acoustic Manipulation of Nervous Systems"
Uses acoustic signals below conscious threshold to affect neural function
Creates nervous system effects without conscious awareness of stimulus https://patents.google.com/patent/US6017302
DIRECT BRAIN STIMULATION/MODULATION
US3951134 (1976) - "Apparatus and Method for Remotely Monitoring and Altering Brain Waves"
Monitors brain waves via radio signals and can modify them remotely
Early foundation for non-contact brain wave manipulation technology https://patents.google.com/patent/US3951134
US5123899 (1992) - "Method & System for Altering Consciousness"
System for altering neural activity to change conscious states
Applies scientific principles to modify awareness and cognition https://patents.google.com/patent/US5123899
US5356368 (1994) - "Method of and Apparatus for Inducing Desired States of Consciousness"
Creates specific consciousness states through precise stimulation
Can induce targeted mental states from relaxation to heightened alertness https://patents.google.com/patent/US5356368
US6488617 (2002) - "Method & Device for Producing a Desired Brain State"
Technology to induce specific brain states on demand
Creates reproducible neural conditions through external stimulation https://patents.google.com/patent/US6488617
US6135944 (2000) - "Method of Inducing Harmonious States of Being"
Creates states of mental harmony through neurological manipulation
Induces positive emotional and cognitive states through stimulation https://patents.google.com/patent/US6135944
US3712292 (1973) - "Method and Apparatus For Producing Swept Frequency-Modulated Audio Signal Patterns For Inducing Sleep"
Uses frequency-modulated audio to induce sleep states
Creates unconsciousness through carefully designed sound patterns https://patents.google.com/patent/US3712292
US6729337 (2003) - "Sony Brain Waves Manipulation by Ultrasound"
Uses ultrasonic waves to affect brain function
Creates neural effects through non-audible sound frequencies https://patents.google.com/patent/US6729337
Audio Transmission Technologies
DIRECT-TO-BRAIN AUDIO
US4877027 (1989) - "Hearing System"
Microwave auditory effect creating sounds directly in the brain
Bypasses normal hearing organs to transmit sounds through microwave pulses https://patents.google.com/patent/US4877027
US4858612 (1989) - "Hearing Device"
Delivers audio content directly to the brain without passing through ears
Creates perception of sound through direct neural stimulation https://patents.google.com/patent/US4858612
US2995633 (1961) - "Means for Aiding Hearing"
Early technology for enhancing hearing through direct neural interfaces
Bypasses damaged hearing structures through alternative pathways https://patents.google.com/patent/US2995633
US3566347 (1971) - "Psycho-Acoustic Projector"
Projects acoustic signals to create psychological effects in targets
Early military application of directed sound for psychological influence https://patents.google.com/patent/US3566347
US5889870 (1999) - "Acoustic Heterodyne Device & Method"
Creates audible sound through interference patterns of ultrasonic waves
Enables highly directional audio delivery to specific targets https://patents.google.com/patent/US5889870
US6587729 (2003) - "Apparatus for Audibly Communicating Speech Using the Radio Frequency Hearing Effect"
Transmits speech directly into the head using radio frequency pulses
Creates the perception of hearing voices with no actual sound waves https://patents.google.com/patent/US6587729
US6470214 (2002) - "Method & Device for Implementing Radio Frequency Hearing Effect"
Implements the radio frequency hearing effect for communication
Creates perception of sound without acoustic waves https://patents.google.com/patent/US6470214
US5539705 (1996) - "Ultrasonic Speech Translator & Communications System"
Translates speech into ultrasonic frequencies and back to audible
Enables covert communication through non-audible frequency bands https://patents.google.com/patent/US5539705
US6426919 (2002) - "Portable & Hand-Held Device for Making Humanly Audible Sounds Responsive to the Detecting of Ultrasonic Sounds"
Converts ultrasonic signals to audible sound in a portable device
Enables detection of ultrasonic communications or signals https://patents.google.com/patent/US6426919
US6487531 (2002) - "Signal Injection Coupling into the Human Vocal Tract for Robust Audible & Inaudible Voice Recognition"
Injects signals into vocal tract for enhanced voice recognition
Works with both audible and inaudible voice commands https://patents.google.com/patent/US6487531
US5922016 (1999) - "Apparatus for Electric Stimulation of Auditory Nerves of a Human Being"
Directly stimulates auditory nerves using electrical signals
Creates perception of sound through neural pathway activation https://patents.google.com/patent/US5922016
US3647970 (1972) - "Method & System for Simplifying Speech Wave Forms"
Reduces speech to essential components for efficient transmission
Early technology for processing speech for direct neural interfaces https://patents.google.com/patent/US3647970
Brain/Nervous System Monitoring
NEURAL MONITORING SYSTEMS
US5392788 (1995) - "Method and Device for Interpreting Concepts and Conceptual Thought from Brainwave Data"
Extracts and interprets thoughts and concepts from brain wave patterns
Claims to decode the brain's electromagnetic signatures of specific thoughts https://patents.google.com/patent/US5392788
US4958638 (1990) - "Non-Contact Vital Signs Monitor"
Monitors heart rate, breathing, and movement from a distance
Uses radio frequency energy to detect physiological states without contact https://patents.google.com/patent/US4958638
US5788648 (1998) - "Electroencephalographic Apparatus for Exploring Responses to Quantified Stimuli"
Measures brain's electrical responses to specific, measured stimuli
Quantifies neural reactions to various types of sensory input https://patents.google.com/patent/US5788648
US7689272 (2010) - "Nerve Stimulation Functionality Indicator Apparatus & Method"
Monitors and indicates the functionality of nerve stimulation systems
Provides feedback on neural response to stimulation treatments https://patents.google.com/patent/US7689272
US20100324415A1 (2010) - "Platform for Detection of Tissue Structure Change"
Detects changes in tissue structure through non-invasive monitoring
Can identify neural tissue modifications from external sensors https://patents.google.com/patent/US20100324415A1
US20130001422A1 (2013) - "Apparatus & Method for Determining the Condition of a Living Subject"
Advanced system for monitoring physical and neural conditions
Provides detailed assessment of subject state through multiple parameters https://patents.google.com/patent/US20130001422A1
US7811234 (2010) - "Remote Sensing Method & Device"
Advanced method for remotely monitoring physiological and neural activity
Captures detailed biological data without subject awareness or consent https://patents.google.com/patent/US7811234
US6490480 (2002) - "Apparatus & Methods for Measuring Autonomic Nervous System Function"
Measures involuntary nervous system functions remotely
Assesses stress, emotional states, and physiological responses https://patents.google.com/patent/US6490480
US5507291 (1996) - "Method and an Associated Apparatus for Remotely Determining Information as to Person's Emotional State"
Remotely detects and analyzes emotional states through physiological signs
Provides assessment of emotional condition without direct contact https://patents.google.com/patent/US5507291
US6292688 (2001) - "Method & Apparatus for Analyzing Neurological Response to Emotion-Inducing Stimuli"
Analyzes neural patterns produced in response to emotional triggers
Maps how the brain processes emotional stimuli for potential manipulation https://patents.google.com/patent/US6292688
US6011991 (2000) - "Layout Overlap Detection with Selective Flattening in Computer Implemented Integrated Circuit Design"
Identifies overlapping patterns in neural network design
Enables optimization of artificial neural systems based on brain patterns https://patents.google.com/patent/US6011991
EMOTIONAL/VOICE ANALYSIS
US8965770 (2015) - "Detecting Emotion in Voice Signals in a Call Center"
Analyzes emotional states from voice patterns in real-time
Enables targeted responses based on detected emotional vulnerabilities https://patents.google.com/patent/US8965770
US20020002464A1 (2002) - "System & Method for a Telephonic Emotion Detection that Provides Operator Feedback"
Detects emotional states through telephone voice analysis
Provides feedback to operators for adapting to caller's emotional state https://patents.google.com/patent/US20020002464A1
US6006188 (1999) - "Speech Signal Processing for Determining Psychological or Physiological Characteristics"
Extracts psychological and physiological data from speech patterns
Enables assessment of mental and physical states through voice analysis https://patents.google.com/patent/US6006188
Commercial Application & Integration
CONSUMER PRODUCTS WITH NEURAL INTERFACE
US20230225659A1 (2023) - "Systems for Acquiring EEG Data" (Apple)
AirPods capable of monitoring brain activity through skin contact
Presents brain monitoring as a health feature while collecting neural data https://patents.google.com/patent/US20230225659A1
US6039688 (2000) - "Therapeutic Behavior Modification Program, Compliance Monitoring and Feedback System"
Commercial system for behavior modification with neural monitoring
Tracks compliance with therapeutic programs through physiological signs https://patents.google.com/patent/US6039688
US6239705 (2001) - "Behavior Modification"
Consumer product designed to alter behavior patterns
Uses neural feedback to reinforce desired behavioral changes https://patents.google.com/patent/US6239705
US6164284 (2000) - "System of Implantable Devices for Monitoring and/or Affecting Body Parameters"
Network of implanted devices to monitor and modify body functions
Creates internal web of sensors and stimulators for physiological control https://patents.google.com/patent/US6164284
US20130297301A1 (2013) - "Coupling an Electronic Skin Tattoo to a Mobile Communication Device"
Electronic tattoo that adheres to the throat to capture voice commands
Includes galvanic skin response detector to analyze emotional states https://patents.google.com/patent/US20130297301A1
US6239705 (2001) - "Intra-Oral Electronic Tracking Device"
Electronic tracking device designed for placement inside the mouth
Enables covert monitoring of location and potentially physiological data https://patents.google.com/patent/US6239705
MEDICAL/THERAPEUTIC APPLICATIONS
US8892208 (2014) - "Closed Loop Neural Stimulation"
Fully automated neural stimulation system with sensor feedback
Continuously adjusts neural stimulation based on monitored responses https://patents.google.com/patent/US8892208
US9433789 (2016) - "Method, System & Apparatus for Remote Neural Modulation Brain Stimulation and Feedback Control"
Remote stimulation and modulation of neural activity with feedback control
Medical legitimization of direct brain manipulation technology https://patents.google.com/patent/US9433789
US5522865 (1996) - "Voltage/Current Control System For Human Tissue Simulator"
Precisely controls electrical stimulation parameters for neural tissue
Creates reproducible effects in human tissue through calibrated simulation https://patents.google.com/patent/US5522865
US4227516 (1980) - "Apparatus For Electrophysiological Stimulation"
Early device for electrical stimulation of physiological processes
Creates targeted neural effects through precisely controlled currents https://patents.google.com/patent/US4227516
US4335710 (1982) - "Device for the Induction of Specific Brain Wave Patterns"
Medical device that induces specific brainwave patterns for therapy
Creates desired neural oscillation patterns for treatment purposes https://patents.google.com/patent/US4335710
US5036858 (1991) - "Method and Apparatus For Changing Brain Wave Frequency"
Therapeutic technique for altering dominant brainwave frequencies
Enables shifting between different mental states for clinical benefit https://patents.google.com/patent/US5036858
US5076281 (1991) - "Device and Method for Effecting Rhythmic Body Activity"
Induces rhythmic physiological functions through neural stimulation
Creates synchronized body rhythms for therapeutic purposes https://patents.google.com/patent/US5076281
US3782006 (1974) - "Means and Methods to Assist People in Building Up An Aversion to Undesirable Habits"
Behavior modification system using aversive neural conditioning
Creates negative associations with targeted behaviors through stimulation https://patents.google.com/patent/US3782006
US3727616 (1973) - "Electronic System For The Stimulation of Biological Systems"
Early electronic system for stimulating biological functions
Enables control of physiological processes through targeted signals https://patents.google.com/patent/US3727616
Tracking, Surveillance & Identification
TRACKING SYSTEMS
US5211129 (1993) - "Syringe-Implantable Identification Transponder"
Injectable RFID transponder for identification and tracking
Originally for animals but applicable to human tracking https://patents.google.com/patent/US5211129
US7076441 (2006) - "Identification and Tracking of Persons Using RFID-Tagged Items In Store Environments"
Tracks individuals' movements and behaviors in retail environments
Links RFID data from products to individual consumer profiles https://patents.google.com/patent/US7076441
US6014080 (2000) - "Body Worn Active and Passive Tracking Device"
Wearable device that enables continuous tracking of individuals
Combines active and passive technologies for reliable monitoring https://patents.google.com/patent/US6014080
US5868100 (1999) - "Fenceless Animal Control System Using GPS Location Information"
Tracking and control system using GPS location data
Creates virtual boundaries with enforcement through neural stimulation https://patents.google.com/patent/US5868100
US6873261 (2005) - "Early Warning Near-Real-Time Security System"
Security monitoring system with near-real-time alerts
Enables rapid response to detected anomalies or threats https://patents.google.com/patent/US6873261
US20080282817A1 (2008) - "Remote Monitoring of Fixed Structures"
System for continuous remote monitoring of buildings and infrastructure
Enables surveillance of structural integrity and occupancy patterns https://patents.google.com/patent/US20080282817A1
US6947978 (2005) - "Method for Geolocating Logical Network Addresses"
Tracks geographical location based on network address information
Enables physical location identification of digital presences https://patents.google.com/patent/US6947978
US7805291 (2010) - "Method of Identifying Topic of Text Using Nouns"
Analyzes text content to identify subject matter through noun patterns
Enables automated categorization and monitoring of textual communications https://patents.google.com/patent/US7805291
MONITORING & SURVEILLANCE TECHNOLOGY
US8362884 (2013) - "Radiant Electromagnetic Energy Management"
Controls and directs electromagnetic fields for surveillance applications
Advanced management of EM energy for sensing and monitoring https://patents.google.com/patent/US8362884
US20090257555A1 (2009) - "X-Ray Inspection Trailer"
Mobile X-ray scanning system for surveillance applications
Enables covert inspection through walls and other barriers https://patents.google.com/patent/US20090257555A1
US20120104282 (2012) - "Target Tracking System & Method with Jitter Reduction Suitable for Directed Energy Systems"
Advanced tracking system optimized for directed energy applications
Maintains lock on human targets with minimized tracking errors https://patents.google.com/patent/US20120104282
US20090172539A1 (2009) - "Conversation Abstractions Based on Trust Levels in a Virtual World"
Monitors and categorizes virtual conversations based on trust metrics
Creates surveillance system for virtual environments and communications https://patents.google.com/patent/US20090172539A1
US8479225 (2013) - "Social and Interactive Applications for Mass Media"
System for integrating surveillance and influence through mass media
Creates interactive applications that monitor user responses while delivering content
https://patents.google.com/patent/US8479225
US6245531 (2001) - "Polynucleotide Encoding Insect Ecdysone Receptor"
Genetic technology related to insect hormone receptors
Potential application for biological monitoring or control systems https://patents.google.com/patent/US6245531
Mind-Machine Interface
BRAIN-COMPUTER INTERFACE
US8477392 (2013) - "Brain-Machine Interface Systems and Methods"
Creates direct interface between neural activity and external devices
Enables both monitoring and potential influence of brain function https://patents.google.com/patent/US8477392
US6529773 (2003) - "Communication and Control by Means of Brainwave and other Process causing Voltage changes"
Enables control of external devices through brain signals
Interprets neural voltage changes into machine-readable commands https://patents.google.com/patent/US6529773
US3967616 (1976) - "Multichannel System For And A Multifactorial Method of Controlling the Nervous System of a Living Organism"
Early multichannel system for complex nervous system control
Creates sophisticated influence over neural function through multiple pathways https://patents.google.com/patent/US3967616
DIRECTED ENERGY SYSTEMS
US4700068 (1987) - "Apparatus & Method for Spatially Characterizing & Controlling a Particle Beam"
Precisely controls and directs particle beams for targeted applications
Enables accurate delivery of particle energy to specific locations https://patents.google.com/patent/US4700068
US7405834 (2008) - "Compensated Coherent Imaging for Improved Imaging & Directed Energy Weapons Applications"
Enhanced imaging system optimized for directed energy weapons
Improves targeting accuracy and effect assessment capabilities https://patents.google.com/patent/US7405834
US7609001 (2009) - "Optical Magnetron for High Efficiency Production of Optical Radiation & Related Methods of Use"
Generates high-efficiency optical radiation for directed energy applications
Creates powerful light-based energy projection capabilities https://patents.google.com/patent/US7609001
US8049173 (2011) - "Dual Use RF Directed Energy Weapon and Imager"
Combined energy weapon and imaging system in a single platform
Can both scan/monitor targets and deliver directed energy effects https://patents.google.com/patent/US8049173
US20120274147A1 (2012) - "Wireless Energy Transmission Using Near-Field Energy"
Transmits energy wirelessly through near-field coupling
Enables remote power delivery for covert or embedded systems https://patents.google.com/patent/US20120274147A1
US7282727 (2007) - "Electron Beam Directed Energy Device & Methods of Using Same"
Directs concentrated electron beams for energy delivery applications
Creates focused effects through precision electron stream control https://patents.google.com/patent/US7282727
US4959559 (1990) - "Electromagnetic or Other Directed Energy Pulse Launcher"
Launches concentrated pulses of directed electromagnetic energy
Creates powerful, focused energy effects at a distance https://patents.google.com/patent/US4959559
US7629918 (2009) - "Multifunctional Radio Frequency Directed Energy System"
Versatile system combining multiple RF directed energy capabilities
Integrates various energy projection technologies in a single platform https://patents.google.com/patent/US7629918
EP2113063B1 (2009) - "Energy Focusing System for Active Denial Apparatus"
Focuses electromagnetic energy for "active denial" applications
Creates directed energy fields that affect human subjects at a distance https://patents.google.com/patent/EP2113063B1
US2860627 (1958) - "Pattern Photic Simulator"
Early system for creating patterned light stimulation
Induces neural effects through rhythmic visual patterns https://patents.google.com/patent/US2860627









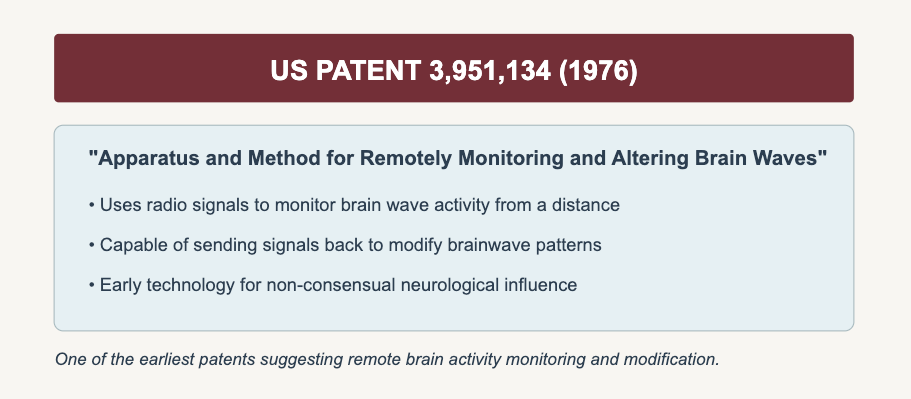








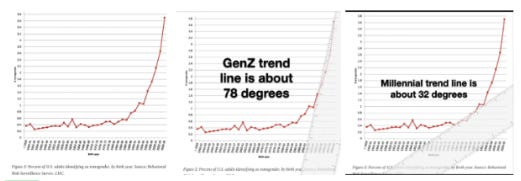




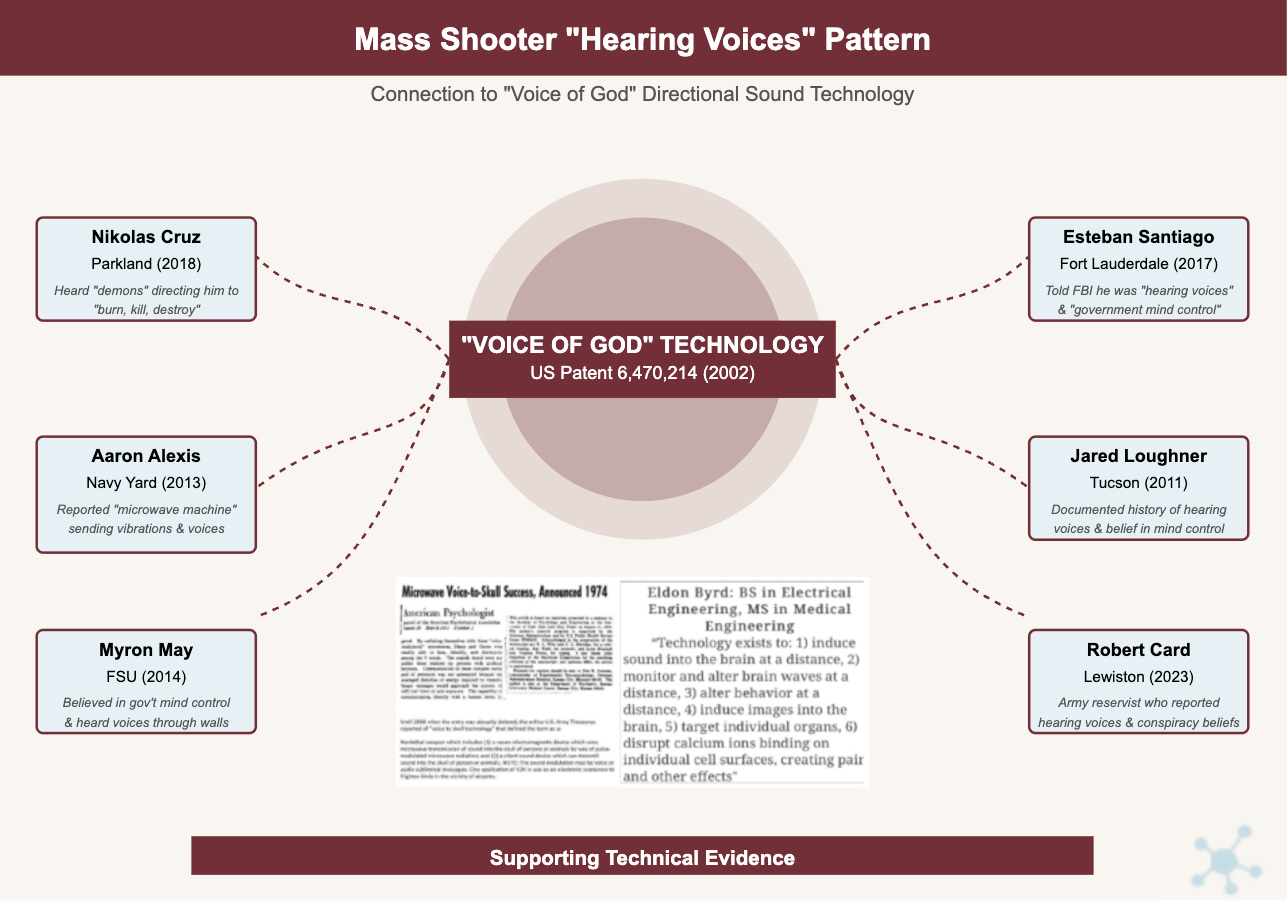









“Next time your phone buzzes, recognize beyond the addiction pattern...”.
Next time your phone buzzes, throw the damn thing in the trash where it belongs. I don’t want to hear about ‘convenience’ and ‘the necessity to have one’. That's making excuses for the devil in your hand.
The bottom line is that these have become tools of destruction to steal away your humanity and suck the life and soul right out of your heavily-addicted body.
There is nothing wrong with Smart Tech at the basic level. These are tools to be used like your toaster or can opener. But that is when these are used with neutral or even positive intent. These devices could have been designed and used for The Good and the benefit of the human family that craves real connection among ourselves and not the phony ‘connections’ of emails and texts and videos and the addiction of craving ‘Likes’ and the approval of others.
Instead, those who produce these digital demons and those run the internet platforms and those who work without stop to control narratives (and YOUR mind and to conjure non-truths as ‘truth’ have nothing with bad intent in their hearts and minds.
Stay addicted if you like. That’s your choice. But realize that every single moment you spend on your Not-So-Smart-To-Have-Phone is not only one less moment of Life you will experience and that you are robbing yourself of real experiences and real things... but that with every moment that goes by you have much less life energy and that much left of what is left of your mind and soul.
You think the cellphone bill you pay every month is too high? That’s not the half of it. The cost is your very soul. But it seems that many people already have decided that their soul has no value anyway so what's the harm.
Going through your life with your eyes glued to a tiny screen and a dead and blank look on your ashen face and a device permanently attached to your betraying hand? Locked into a dead and programmed moment that seems to last forever. With no reflections about the past... no reality in your present moment... and no thoughts about the future. You have now been fully programmed from being live, flesh-and-blood person to a THING. An object. Just something to be manipulated by hidden forces that hate you.
Yes, it’s that bad.
Hard not to notice how carefully you’ve written this. It speaks to the communication minefield that’s been embedded beneath all our digital communication. You write knowing that there’s an audience out that that has been primed to misunderstand and we’ve all been trained to communicate more carefully. It’s the new self defense against thought crimes. Just another layer as I read all of this.
Astonishing, resonant work, Josh!
It also makes me think of how shamed judgement and perceptions about lack of forgiveness are woven into the matrix. The cultural autoimmunity we’re all living in now.
Hope you’re balancing all of this powerful research with some good heart-to-heart, one-on-one connection… but I suspect that’s what powers you ultimately. 🙏